Disrupting the Kill Chain with WithSecure™ Cloud Protection for Salesforce

Landscape Overview
Salesforce Cloud applications like Sales Cloud, Service Cloud or Experience Cloud are now a business-critical service for organizations across a wide range of industries and verticals. Unfortunately, their popularity has attracted the attention of cyber criminals looking to use them as a way to illegitimately gain access to these companies’ data and networks.
Cloud computing has become an increasingly popular means of storing and accessing data remotely. As one of the leading vendors of cloud-based CRM solutions and other valuable business apps, Salesforce has implemented strict security measures to protect its cloud and network infrastructure. In the cloud realm, a shared responsibility model defines the security responsibilities of both cloud providers and consumers. Under this model, the data owner holds the primary responsibility of securing data that flows in and out of their Salesforce environment.
The business benefits of using cloud-based applications like Salesforce are huge and hugely outweigh the additional security risks they introduce. However,it is essential that you are aware of the nature and extent of these risks so you can decide what action you need to take to mitigate them.
If you want to proactively secure your Salesforce Cloud environment, it is important to understand the methods attackers are using and what can be done to combat them. These methods range from phishing and sending malicious urls via email to social engineering and taking advantage of client-facing platforms to directly upload weaponized content to the cloud.
In this whitepaper we'll break down three of the most typical attack scenarios by looking at what cyber security experts call the "Kill Chain". We will also discuss how WithSecureTM can help to disrupt that Kill Chain with the solution designed for Salesforce Cloud.
Threat actors: who wants to steal our data and why?
As more and more businesses have shifted their operations to the cloud, criminals have become aware that large troves of valuable and sensitive data are held in cloud environments. However, different threat actors have very different motivations and levels of sophistication, and it is important to understand who they are and why they might be attacking you.
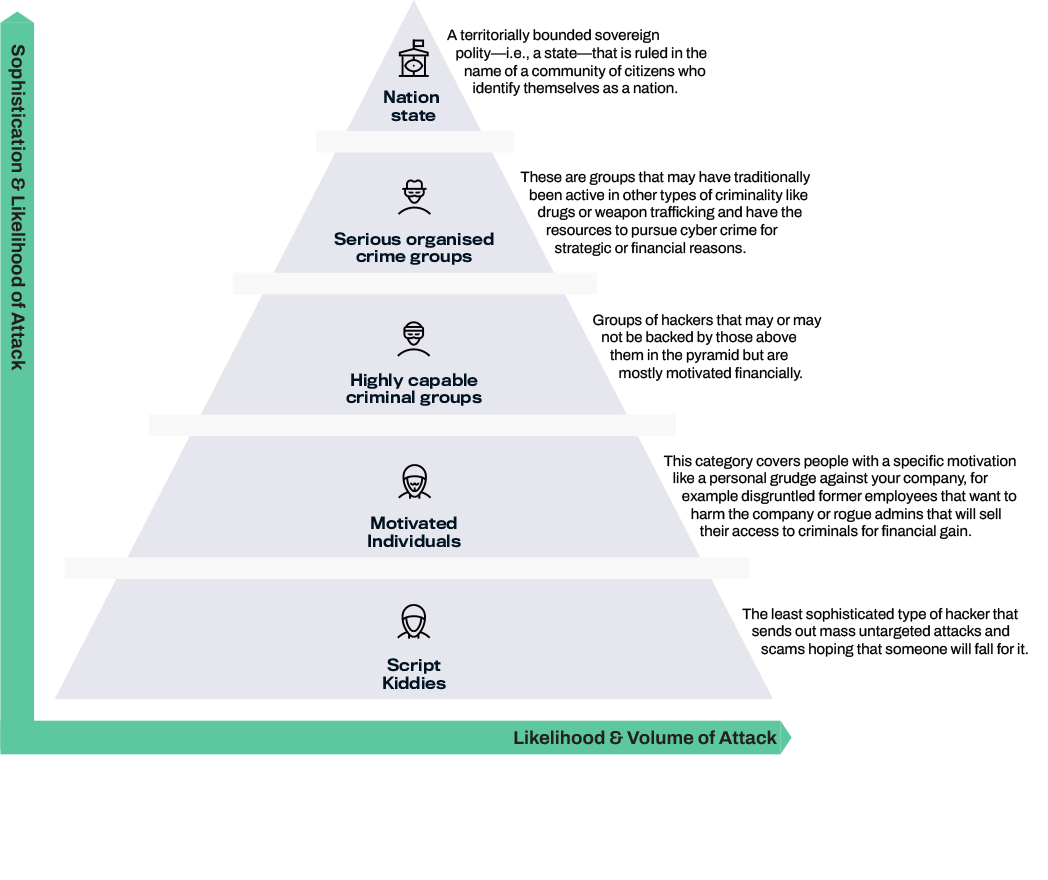
The pyramid above demonstrates the hierarchy of attackers. If you’re targeted by one of the actors at the top, they’re very likely to succeed, nation states and serious organized crime groups have huge resources to put behind acquiring data that they have identified as strategically important. In general, the larger the organization the higher the likelihood is of them being attacked.
Basic cyber training and antivirus software will likely protect you from most of what comes from the base of the pyramid, so it’s the middle that represents the biggest threat to most small and medium-sized organizations.
The cyber Kill Chain
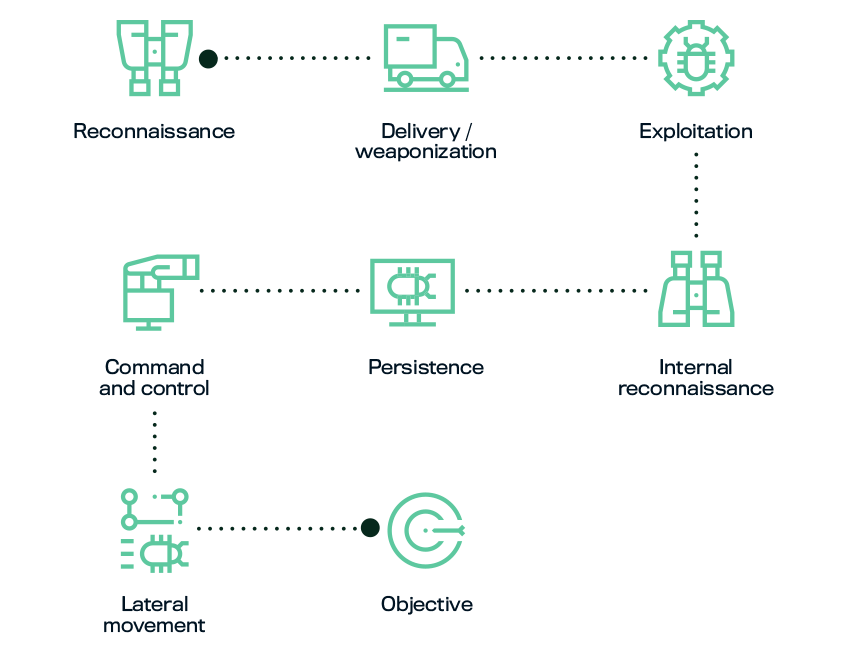
Using the Kill Chain to assess how an advanced threat actor would approach your organization makes it easier to understand which steps, at a minimum, an attacker would have to take to succeed in an attack against your company. This allows you to build preventative or detective controls to counter them.
The WithSecure™ Kill Chain model is adapted from one originally created by Lockheed-Martin that is widely used and accepted in the industry. We have added some additional steps from our own experience of researching and combatting attacks.
The other end of the spectrum
If none of the above applies, then there’s MDR. On-premise IT, the need to fulfill new security requirements as part of an ISO27001 accreditation, false positive rates of over 10% and threats from within and without all lend themselves to an MDR approach, especially one with some serious UEBA (User Entity and Behavior Analytics) chops. The same applies if you’re struggling with hiring or retaining skilled staff: assured response, the need to free up your existing IT security resource or the need to increase the capability of your team are all indicators that MDR might be the right option. The same applies if there’s no institutional threat hunting knowledge or if your security team can’t respond to alerts: MDR, either our own Countercept MDR or a managed EDR service from one of our partners, may well fit the bill. Local partners providing MDR are particularly valuable in situations where your organization has industry-specific requirements or prefers services delivered in languages other than international English. If a 24/7 service is not vital, a partner managed service is also appropriate in some cases. Finally, if you value a continuous feed of security insights and posture improvement recommendations when your organization isn’t under attack, then Countercept MDR is a really good fit; our threat hunters spend a great deal of their time researching threats and thinking like attackers, and passing these insights on to customers is part of their job.
What happens during each phase of the kill chain
External vs internal threats
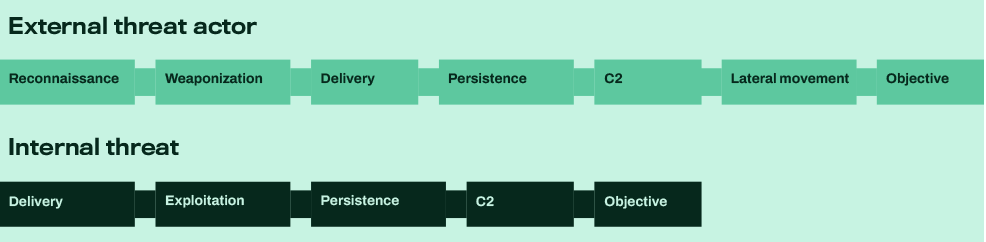
At WithSecure™ we distinguish between internal and external threats, based on the initial method of infiltration which takes place prior to or simultaneously with the reconnaissance and weaponization phases.
An external threat is typified by an attacker that seeks to “become your customer” or gain trust in a similar way. Imagine a recruitment firm that takes on a new candidate not knowing that this person is really a cybercriminal. The attacker would likely send a real CV initially and exchange non-infected emails to build trust before weaponizing and carrying out an attack later.
An internal threat on the other hand has an attacker that already has access on behalf of the internal user. Maybe they bought it, either directly or online, or maybe they stole it using a phishing attack. Either way they can easily skip to delivery with very specific targeting.
The Kill Chain framework is not a one-size-fits-all solution for all types of cyberattacks. Some attacks may skip certain stages entirely, or use different techniques to achieve their objectives. However, understanding the Kill Chain framework and how different threat actors may approach each stage can help organizations better prepare for and defend against cyberattacks.
Salesforce Kill Chain examples
Attacking via Community portal
This is an example of an external Kill Chain, the attacker is acting as a member of your community who would have legitimate access to your Community Portal.
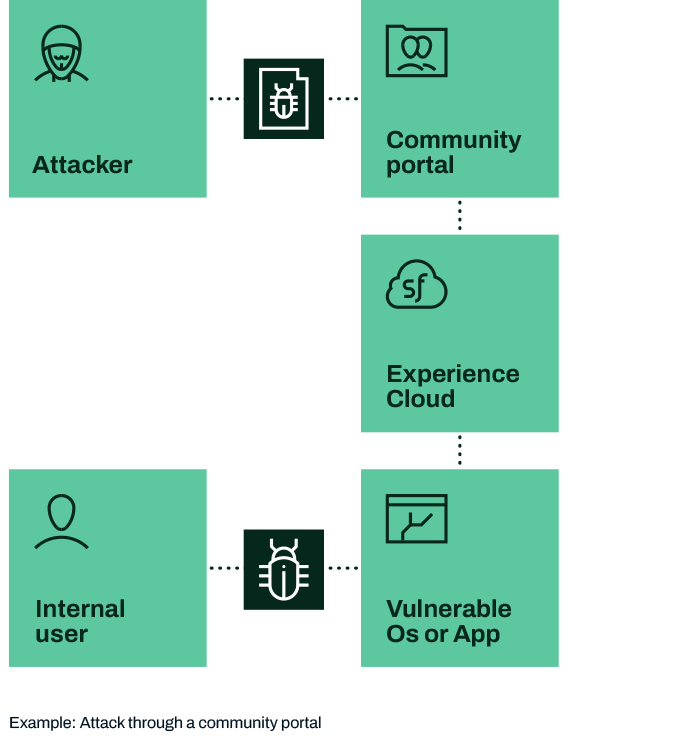
Reconnaissance: The attacker registers and creates a new user account in the community portal.
Weaponization: The attacker creates a weaponized document with a vulnerability exploit.
Delivery: The attacker uploads the weaponized file to the community portal. The file is saved in Salesforce Experience Cloud.
Exploitation: Failing intervention an internal user opens the file and the weaponized payload is executed within the vulnerable application on their device.
C2 / Persistence: The attacker now has access to this user’s device and can proceed to lateral movement.
Objective: The attacker works to ex-filtrate confidential or sensitive data from the organization.
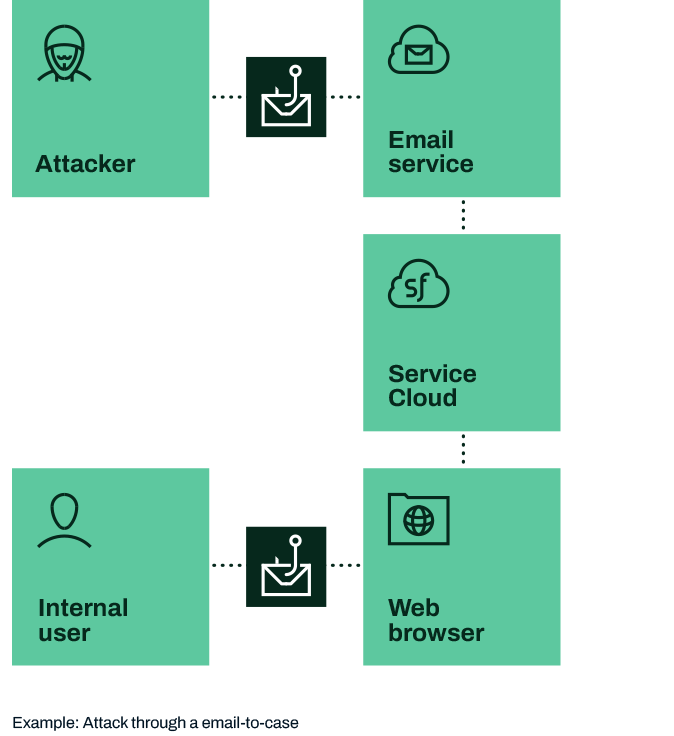
Exploiting email-to-case
This is another external Kill Chain, where an attacker uses email-to-case to penetrate via Salesforce Service Cloud. They will be posing as a customer or user of your service.
Reconnaissance: The attacker finds out the email address used for sending customer support requests.
Delivery: The attacker creates a website for a phishing attack and sends the link in an email message to create an email-to-case request for customer support. The link is saved in the Salesforce org.
Weaponization: The attacker waits a while and then adds the malicious code to the website they have created.
Exploitation: Failing intervention an internal user opens the link and the malicious is executed within the vulnerable application on their device.
C2 / Persistence: The attacker now has access to this user’s device and can proceed to lateral movement.
Objective: The attacker works to ex-filtrate confidential or sensitive data from the organization.
Supply chain attack
Salesforce supports various ways to integrate with, and extend the capabilities of the Salesforce Lightning platform. Organizations may use solutions that can create, update and read content and these solutions would use native Salesforce APIs that are trusted by default. This Kill Chain shows how an attacker could use a third-party application to breach Salesforce Lightning.
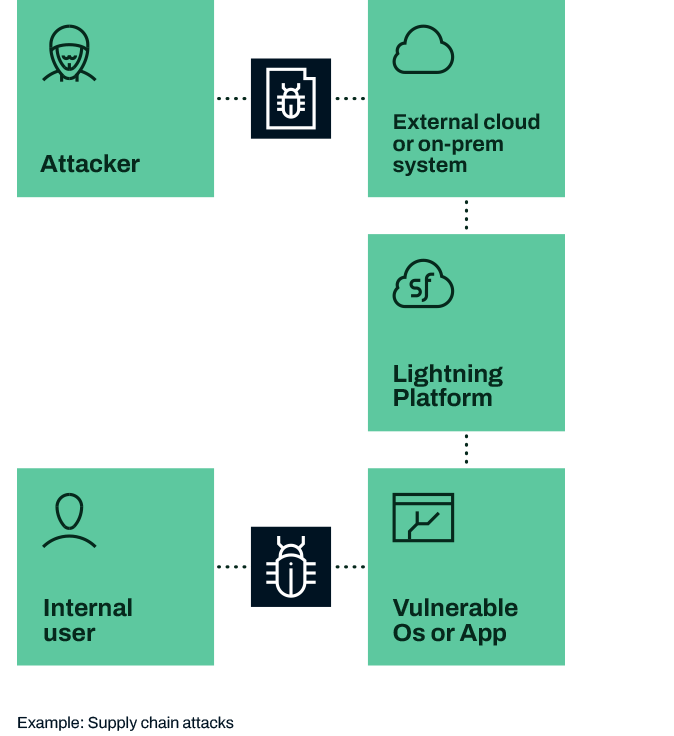
Reconnaissance: The attacker discovers an exploit AppExchange app or compromises an external system that your organization is using that has integration with Salesforce Lightning. s to Salesforce.
Weaponization: The attacker creates a weaponized document with a vulnerability exploit or malicious payload.
Delivery: The attacker pushes the weaponized file through the thirdparty application. The file will be trusted by default because it comes from a whitelisted source.
Exploitation: Failing intervention an internal user opens the file and the weaponized payload is executed.
C2 / Persistence: The attacker now has access to this user’s device and can proceed to lateral movement
Objective: The attacker works to ex-filtrate confidential or sensitive data from the organization.

Want to know more about the topic
Product introduction
WithSecure's Cloud Protection for Salesforce effectively combats all the previously mentioned attack scenarios, and more. Our solution actively scans files and URLs every time they are uploaded to, downloaded from or clicked on within Salesforce, providing real-time detection and blocking of malicious content, including malware and phishing links.
Our Cloud Protection solution is particularly effective against advanced attack methods like the email-to-case approach, where attackers use dormant malicious payloads to evade security systems.
Working alongside Salesforce, our Cloud Protection solution is designed to complement their security capabilities, with no overlap between our solution and Salesforce's built-in or add-on security tools. With our click-and-go deployment, you get instant protection without any tedious deployment projects.
Additionally, our solution provides constant visibility into your content security status and offers comprehensive reports and analytics to help you hunt threats. Plus, integrating it into your SIEM is easy.
When it comes to defending against sophisticated cyber attacks, it's crucial to have security measures in place across multiple fronts and layers. This includes systematically addressing vulnerabilities, implementing preventive threat protection on devices and cloud applications, and responding quickly to threats to minimize damages.
Related resources
Secure your Salesforce today.
Tailored for high compliance sectors, our certified solution safeguards Salesforce clouds for global enterprises, including finance, healthcare, and the public sector.
Fill the form and get:
- Free 15-day trial
- Personalized Salesforce security risk assessment report
- Demo and a solution consultation
- Support from our dedicated experts with setup and configurations