We can’t fight ransomware on our own.
It’s time to work together to make our businesses less attractive to criminals.

In 2020 Ransomware changed. The response of most organizations in the UK and the EU did not.
The cyber security industry kept issuing advisories on how organizations could protect themselves, and those organizations continued to struggle in private when they fell victim to attacks. The risks kept rising, and the costs of being attacked showed no signs of going down.
Other things changed too. In the EU, the digital operational resilience act (DORA) gathered momentum, potentially offering European Financial institutions a chance to rethink cyber security regulation and reporting. In the UK, Brexit’s eventual arrival created opportunities for reviewing data protection laws.
Could this changing landscape offer us a chance to fight back against ransomware?
We think so, but it’s going to require teamwork.
Businesses, trade bodies, policy makers, and regulators are all going to have to join in unison. It’s a tough ask, but if it happened, we would have a chance to reduce the return on investment for cyber criminals, and make Europe as a whole a less attractive target. In short, we could lower our risk exposure and reduce our costs.
"It's a tough ask, but if it happened, we would have a chance to reduce the return on investment for cyber criminals."
Here’s why we think this strategy might just work
In the last year we have seen the rise of what some are calling Ransomware 2.0, an evolution of cyber crime defined by two main developments. First, criminals have taken to hunting ‘big game’: large and cash-rich enterprises. This means that ransomware attacks are increasingly targeted, and are driven by the criminals’ assessment of the likely costs and returns of launching a hands-on-keyboard attack. Second, the ransomware gangs have embarked on a tactic of double extortion, by exfiltrating and then threatening to release confidential data if their demands are not met.
In fact, there’s good reason to suspect that in some recent high-profile cases – for example the attack on video game developer CD Projekt Red in February – attackers have treated the encryption of a victim’s files only as a show of strength, their ultimate goal being to force a payment in return for not releasing sensitive data.
It is fair to say that the term ‘ransomware’ no longer does a good job of describing this type of attack. The criminals are instead running protection rackets, which prey on organizations’ fears of exposure, data breaches, and regulatory fines. If the history of protection rackets and the mafias who run them can tell us anything, it is that they cannot be defended against by businesses acting alone.
“... the term ‘ransomware’ no longer does a good job of describing this type of attack. The criminals are instead running protection rackets …"
Sounds like bad news? It is, but we still think there’s a silver lining. The added costs of running Ransomware 2.0 campaigns mean that attackers have to choose which targets they invest in with care. We can use this against them. We can change our behaviors to raise their costs even higher and lower their rewards, and if we can do this in a coordinated way across a territory, then there’s a chance that we could make the entire region less attractive to attackers.
Of course, whenever somebody suggests something like this, the conversation usually turns to banning ransomware payments, just as some countries currently refuse to pay ransoms to kidnappers in the belief that it will make their citizens less likely to be abducted. Not only, the argument goes, would this disincentivize ransomware attacks, but it would prevent the funding of organized crime. The US has already imposed a partial ban by making it illegal to pay money to a sanctioned group, and there is evidence that it is forcing a change in attackers’ tactics.
The thing is, we’ve worked with enough clients who’ve been the victims of ransomware to know a ban can do more harm than good. It can lead to higher costs for victims, it can remove a vital means through which essential (and sometimes lifesaving) services can be brought back online, and in the case of a partial ban (such as that in the US), it places a further decision-making burden on a victim organization. After all, how is a private company supposed to work out whether the anonymous group who are blackmailing them is sanctioned or not?
In short, a ban could pit industry against regulators in a way that would benefit nobody. There are nonetheless plenty of collective actions we can take to either raise the costs of doing crime or lower its rewards.
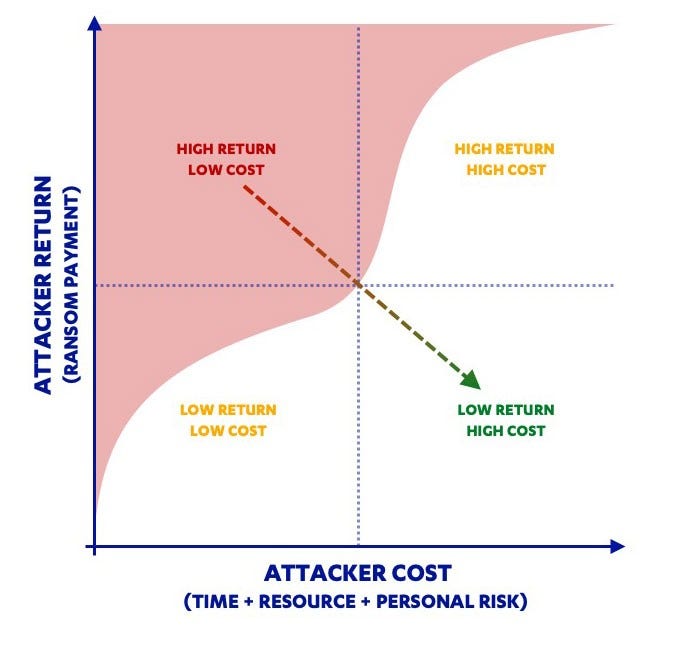
Fig. 1. Right now, ransomware operators face low costs and high rewards. Some of the measures that we can take will increase their costs (and their risks). Others will reduce their rewards. If we can combine these through unified action, we might just be able to force the criminals into a low reward/high cost position from where they no longer see us as attractive targets.
Here are some of our suggestions on where to start:
Lowering the rewards of crime
1. A little tax here; a little incentive there
One recent academic article suggests taxing ransomware payments and providing government-backed financial support to firms who refuse to pay. Obviously, governments across Europe would need to be careful about implementing this legislation, for example, by only giving support to firms who can demonstrate that they took precautions in advance of the attack. Nonetheless, if done well, it would have the effect of disincentivizing ransom payments and thus making European entities less attractive as targets. Taxation would also help bring payments out of the dark, reducing the culture of secrecy that surrounds ransomware victimhood, thus further reducing the symbolic threat upon which attackers rely.
2. Flexible implementation of GDPR
GDPR is important for protecting consumer rights, but it’s not perfect for managing cybercrime. Why is this? Criminal gangs have realized that real profit is to be made preying upon their victims’ fear of regulatory fines, and in the last year these gangs have started to weaponize GDPR as a way of encouraging organizations to pay up. This has been made possible because of the data exfiltration (and threat of release) that is now typical of Ransomware 2.0. Victims consequently find themselves caught between a rock (the criminal gang) and a hard place (GDPR).
Perhaps the best way of combating this criminal tactic is by furthering the regulators’ current flexible approach to imposing fines. Last October, for example, the Information Commissioner’s Office in the UK fined the airline BA a record £20m for data breaches related to a cyber-attack. Although unprecedented in the UK, this figure had actually been negotiated down from an original fine of £183.39m, partly because of the economic impact of COVID-19 on BA.
By explicitly and publicly demonstrating their willingness to enter into dialogue with organizations who have been ransomed, regulators can prevent their punitive measures from being used by criminals. We’re not necessarily saying that regulators should lower their fines to below the ransom demands being issued by criminals, but flexibility in implementation certainly removes some bargaining power from the enemy’s hands.
3. Allow some anonymity
Regulatory fines and reputational damage can be powerful motivators for organizations to sweep ransomware attacks under the carpet, which means that things don’t get reported and knowledge doesn’t get shared. Whatever we might think of the morality of firms of who keep things secret, we wouldn’t be speaking truthfully if we didn’t acknowledge that this happens.
Right now, the EU is considering how to encourage information sharing in article 40 of DORA. The proposals are still not fully formulated. This is an ideal opportunity to work out ways of creating information sharing networks that respect anonymity and enable organizations to share information that could benefit one another without the threat of regulatory action.
Obviously, there would be moral issues to consider here, but it is better than the alternative where organizations suffer in silence. Think of it by analogy to a gun or knife amnesty.
“Taxation would also help bring payments out of the dark, reducing the culture of secrecy that surrounds ransomware victimhood, thus further reducing the symbolic threat upon which attackers rely.”
4. Rethinking insurance
Very few firms admit to giving in to ransom demands, but a surprising number still do. Of course, it’s not actually them paying: in 94% of cases it is the insurance company. In the short term this state of affairs is probably good for individual firms. It is nonetheless not good for European business as a whole. It spreads the cost of ransomware out across an industry and disincentivizes the expensive investments that individual firms should be making to improve their cyber security. Moreover, it gives criminals a reason to keep on attacking.
A simple solution would be to ban insurance cover of ransoms. The problem with this approach is that it would penalize those who did everything right by investing in strong security and incident response, but nonetheless still got hit by ransomware.
A more subtle approach would perhaps be for insurance companies to incentivize investment in security, much as some health insurers now offer discounts to customers who regularly go to the gym. Lower premiums could be offered, for example, to those organizations that made themselves more resilient to a ransomware attack by aligning security investment—such as conducting regular attack simulations— with ransomware risk exposure. Perhaps this would have the added benefit of enabling deeper conversations within organizations between cyber security teams and those who purchase insurance.
Trade and industry bodies could also begin to foster positive steps, for example by making it good cultural practice for firms to publicly declare on their websites that their insurance policies will not cover ransomware payments, thus making them less attractive as targets.
5. Change the culture
There’s a lot of stigma about being a victim of ransomware, and this ultimately benefits criminals who exploit fears of reputational damage.
Obviously, some of this stigma is deserved. Organizations which deal in other people’s data have an obligation to look after it. But in other ways the stigma is increasingly out of place with developments in security. Take the Bank of England’s new approach to resilience as an example: the thinking there is clearly that firms should begin to see cyber attacks as inevitable, and focus on management and response. What if, as an industry, we applied that idea to ransomware?
Is it time, for example, that we began seeing industry awards given to SOCs who successfully responded to, learnt from, and reported ransomware attacks? And whose work perhaps even helped identify the criminal groups who attacked them? Right now, organizations only tend to issue press releases about ransomware attacks when they have absolutely no other choice: what kind of cultural shift would be necessary for us to see routine press statements in which firms discuss ransomware attacks that they rebuffed as an indicator of their resilience?
An organizations’ response to ransomware could even be woven into their corporate social responsibility (CSR) program. They could boast in end-of-year reports of their refusal to give in to ransom demands (and thus fund investment in international crime). They could begin to see resilience in the face of an attack as an ethical virtue. And perhaps – just perhaps – consumers would follow, choosing their banks and insurers on the basis of their ethical record in responding to ransom demands.
Raising the costs of crime
Most of the measures we have so far discussed have been aimed at reducing the rewards of crime, but if we want to make Europe unattractive for big game hunters, then we will also have to increase their costs of doing business here. The key consideration here is making sure that European firms no longer represent low hanging fruit for the attackers. With DORA under consultation, the EU has a historic opportunity to ensure minimum cyber security standards in financial services, whilst an enthusiastic embrace of voluntary testing schemes such as TIBER will ensure that European firms are able to increase their security in a systematic fashion. Right now, too many firms simply assume that they have herd immunity from ransomware, and if events of 2020 have taught us anything, it’s that herd immunity is a bad plan of defense.
But we couldn’t write this article without also asking if it is possible to make things more costly for the attackers at a personal level. After all, who hasn’t smarted at the idea of foreign criminals doing uncountable damage to Europe business and just getting away with it time and time again? The recent news that the US is indicting three North Korean hackers shows that individual criminals operating out of foreign nations can be identified through careful investigation.1 The UK already has in place some legislation to allow targeted sanctions against foreign individuals (so-called ‘Magnitsky’ legislation), and the EU is soon to follow. Currently, Magnitsky legislation is aimed at individual officials responsible for human rights violations. Could we also expand it to cover those responsible for the organizing cyber attacks, or the politicians who hide and enable their activities?
Other mechanisms at our disposal include unexplained wealth orders against individuals who attempt to spend the proceeds of ransoms in European countries. In this case, the onus of proving that the money has not been earned from cyber crime would be shifted to the individual concerned.
“Who hasn’t smarted at the idea of foreign criminals doing uncountable damage to Europe business and just getting away with it time and time again?”
So where do we go from here?
As any CEO or CISO who has dealt with a Ransomware attack will tell you, it can be hugely isolating experience to be ransomed. You have to make the same impossible choices as the thousands who have gone before you, while livelihoods and profits hang in the balance. We don’t think that this is right: we don’t think that the burden of organized crime should be borne in silence. Silence only makes this problem a bigger risk for us all.
Regulation is one important means to combating the threat, and the current changes under consideration in both the UK and the EU offer us a real opportunity to fight back. Nonetheless, this regulation will only succeed if combined with cultural changes to how that organizations prepare for and respond to ransomware. We must understand that when it comes to rebuffing this external threat, competing businesses, regulators and policy makers are all on the same team. The sooner we begin to work together, the quicker we can reduce the enormous costs of ransomware.