Salesforce Data Protection 101 – What is Salesforce security model?
More than 150,000 companies globally now rely on Salesforce for their customer relationship management (CRM) solution. This makes Salesforce the market leader for CRM applications with a market share of 19.5% according to IDC (International Data Corporation) (1).
Its customers are spread across every industry and range from some of the largest and best-known businesses in the world to small and medium-sized businesses and startups. This popularity means that a vast amount of valuable data is stored and managed by Salesforce applications and unfortunately provides an additional attack vector for cyber criminals to target organizations.
Therefore, data security is a top priority for Salesforce and its users, both for economic and regulatory and compliance reasons. It is important that Salesforce users are aware of the Shared Responsibility model that they sign up to when acquiring Salesforce solutions, and uphold their end of it.
Salesforce offers their customers a highly secure cloud infrastructure with a comprehensive set of security controls. However, it is the customer’s responsibility to use these controls, and also to ensure the security of content uploaded to the platform (more on this later).
What Does Salesforce Data Security Looks Like?
In the context of Salesforce, data security essentially means setting up rules and systems to ensure that it is not easy for unauthorized people to access your data. This might sound simple but given the number of users that some organizations need to allow access, getting the right permissions in place requires some careful planning. It is also important that legitimately authorized users are able to easily access the records they need without being overly inconvenienced.
Salesforce has made this process simpler for their users by formulating a data security model that breaks it down into four levels. These four levels make it easier for administrators to set rules and quickly assess the access-level of any particular user, they are as follows:
- Organizational level security
- Object Level security
- Record level Security
- Field level Security
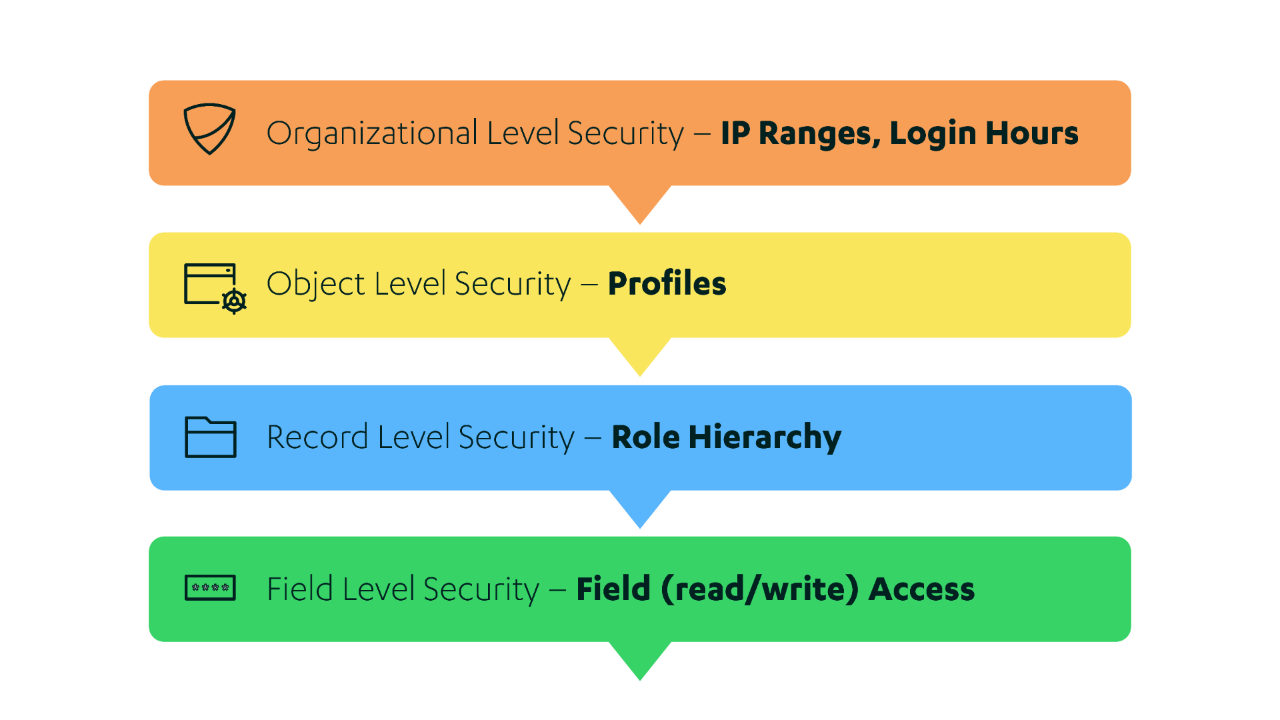
Figure 1: Salesforce security model view
Organizational level
Organizational level security refers to the overall system that your organization has in place for securing its Salesforce environment. At its most basic this means stopping unauthorized users accessing your organization at all. One way of enforcing this is by using Salesforce security controls to restrict the range of trusted IPs that users can login from, meaning that your CRM can only be accessed from certain locations. This can be set in the Login IP Ranges section of a user’s profile. Similarly it is possible to restrict the times that certain users can access your organization, using the Login Hours section.
Other aspects of security that come under the organizational level are ensuring password requirements and deciding on whether to invest in additional security controls such as Salesforce Shield and/or WithSecure's Cloud Protection for Salesforce Solution.
Object level
An object in the context of Salesforce means a domain-level data set. For those familiar with Microsoft Excel or other spreadsheet software, this is analogous to a sheet or a table. In order to access an object, a user needs to be given permission by the administrator.
The old way of doing this was to set a user’s access directly through their profile. It is still important for each user to have a profile set up so that things like Login IP Ranges and Login Hours can be managed from there, but Salesforce no longer recommends using this for setting Object level permissions.
Instead, it is recommended to create Permission Sets and Permission Set Groups, this way you can ensure everyone with a specific job role, for example salesperson, can be easily given access to the contacts and leads they need without having to go through and do it all manually. These permissions can easily be amended and upgraded later.
Field level
A field is an element of an object within Salesforce, it is like a column in our previous spreadsheet analogy. Having access to an object in Salesforce doesn’t necessarily give a user access to all of the fields, so it is important that access is set at the field level as well. Admins can give individual users to read and / or write different fields on an individual basis.
Salesforce recommends managing field level security in the same way as object level, utilizing Permission Sets and Permission Set Groups, but they can also be directly assigned at profile level.
Record level
A record is an individual entry into an object, like a row of information in a spreadsheet. If a user is granted object and field level access, they will be able to enter records into it and view the records they have created. Obviously, this isn’t very useful for collaboration, so setting which other records users can see will be important. Salesforce gives a few ways for you to do this.
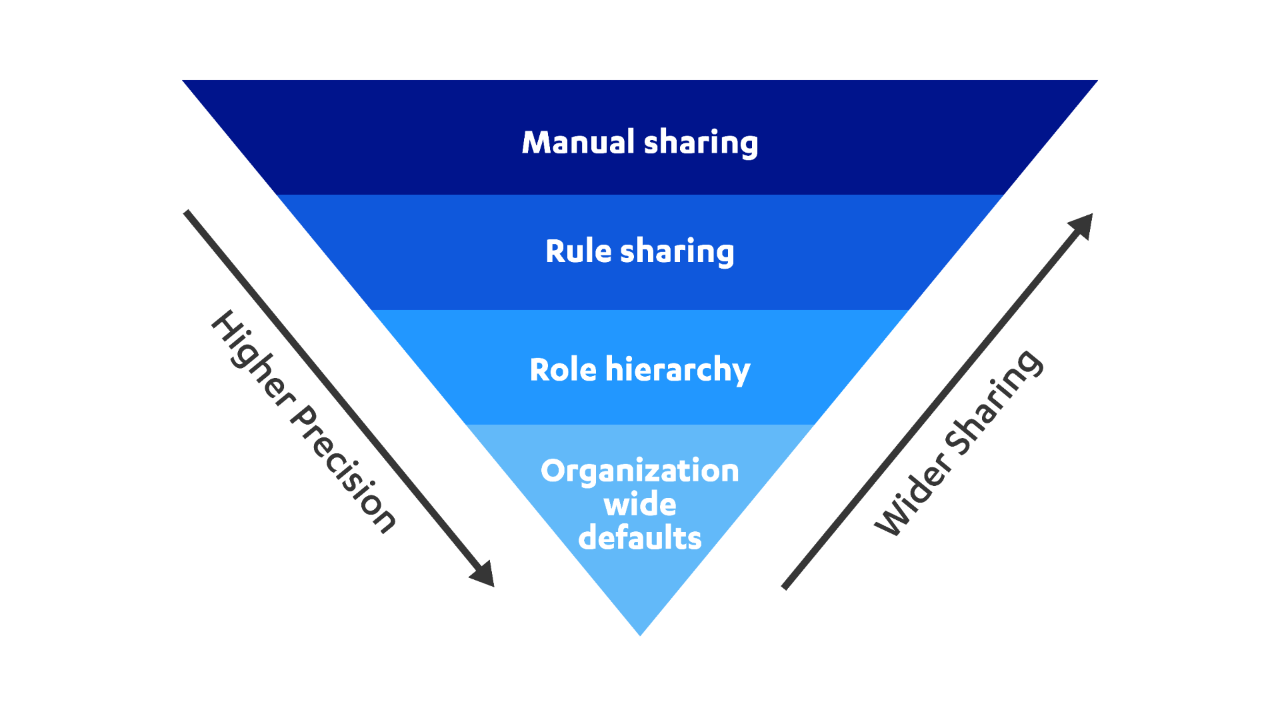
Figure 2: Salesforce record level view
Organization-wide defaults – control the default behavior of how every record is accessed by users who do not own the record. Hence, everyone in the organization gets a level of access to it by default.
Role hierarchy – allows users at the top of the hierarchy to access all records held by users placed below them in the organizational chain by default.
Rule sharing – provides an efficient way to share records laterally and in a makeshift way via public groups. Therefore, allowing a user to share a record automatically with their team.
Manual sharing – allows the owner of certain documents to share it directly with another user(s).
Securing your Salesforce environment from external access
The data model described above deals primarily with how data is accessed, and how permissions are set for internal users. However, admins also need to be aware of how their data could be accessed from the outside, either by its interaction with other Salesforce solutions like Salesforce Community or third-party solutions that can be connected by API.
Salesforce lets you enforce permissions for API and apps in the same way as above, but it is important that these are set with the minimum possible privileges to ensure that they function without giving attackers an easy way in.
Salesforce Shield and WithSecure™ Cloud Protection for Salesforce
Unfortunately, even the best data security policies will not protect you from all attacks. If your organization is targeted by sophisticated criminals, they will likely appear to have legitimate access.
Salesforce Shield helps with this by providing enhancements that elevate the basic encryption of files. This means an extra layer of protection for files that your employees upload to the cloud, so that if this data falls into the wrong hands it is harder to make use of.
WithSecure’s Cloud Protection solution for Salesforce goes one step further than this, providing real time protection from viruses, trojans and ransomware and scanning all content that is uploaded into the cloud.
If you would like to learn more about F-Secure’s Cloud Protection for Salesforce, feel free to download the solution brief. Or start a free trial to test our solution in a live environment.