Ransomware
The biggest cybersecurity threat of 2023 and how to prevent and recover from an attack

A guide by WithSecure experts
Learn how Ransomware works, how it can affect your organization, and what you can do to prevent and recover from an attack. This article provides practical tips and best practices from WithSecure, a leading cybersecurity company.
What is Ransomware?
Ransomware is a type of malicious software (malware) that steals control of the user’s machine or data. Most often, this is done through encrypting data stored on one or more devices. Once the legitimate users’ access is blocked, the attacker offers to restore access for a ransom. Over the past decade, this approach has become an increasingly effective method of online extortion for cybercriminals and other threat actors, which is generally the primary motivation for these attacks.
Encryption is the most well-known method cybercriminals use to pressure victims, but more recently, attackers have adopted secondary extortion methods, such as stealing and leaking the victims’ data before encrypting it.
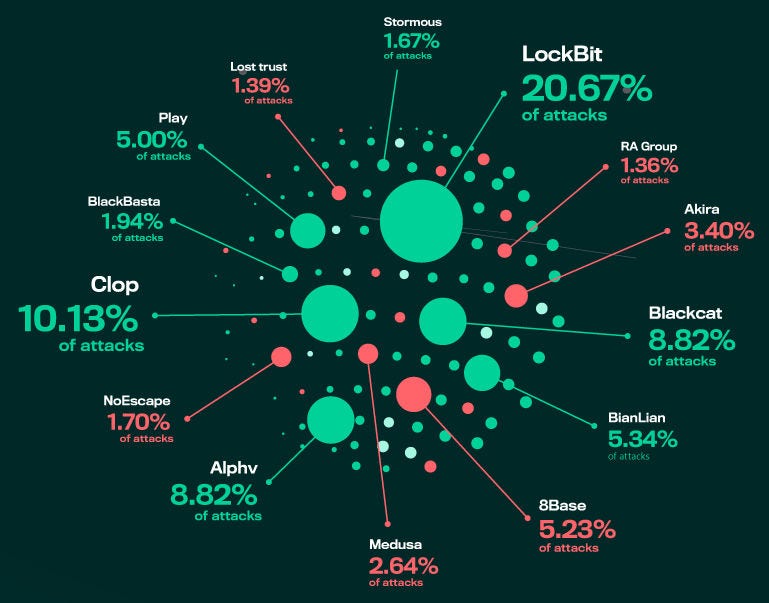
Identifying a Ransomware attack
The most common signs that your organization has become a victim of a ransomware attack are unusual system behavior, such as sluggish performance, crashes, or unresponsive applications. If a system has been encrypted, files and folders will be locked from access.
Altered file extensions, modified desktop elements, and disabled security software are also strong indicators of a ransomware incident. In addition, unusual network traffic or unexpected system changes, like modified wallpapers, further raise suspicion.
Ransom notes in the form of pop-ups or text files often accompany these attacks, demanding payment for decryption.
What can be the outcome of a Ransomware attack?
A ransomware incident can result in severe financial losses for an organization, even without paying the ransom. An attack can lead to a shutdown in operations, which can result in revenue loss. Furthermore, even if the systems are not revenue-generating, having them offline costs the organization vital productivity time.
In addition to direct financial losses, there are also indirect costs. Organizations may not detect an attack in time to stop it, and tight budgets may leave them struggling to find the resources needed to restore operations. Therefore, either directly or otherwise, any financial loss may force the reallocation of funds from one department to another, leading to service disruptions.
Regardless of size or industry, a successful ransomware attack can bring organizations to a standstill. Ransomware infections can often jeopardize a company’s business interests, making it easier for criminals to pressure them into paying the ransom.
Many organizations depend on IT systems and databases to operate; in some cases, they have legal obligations to manage and protect customer data. For these reasons, organizations often feel pressure to resolve ransomware infections quickly (and quietly) by paying the ransom.
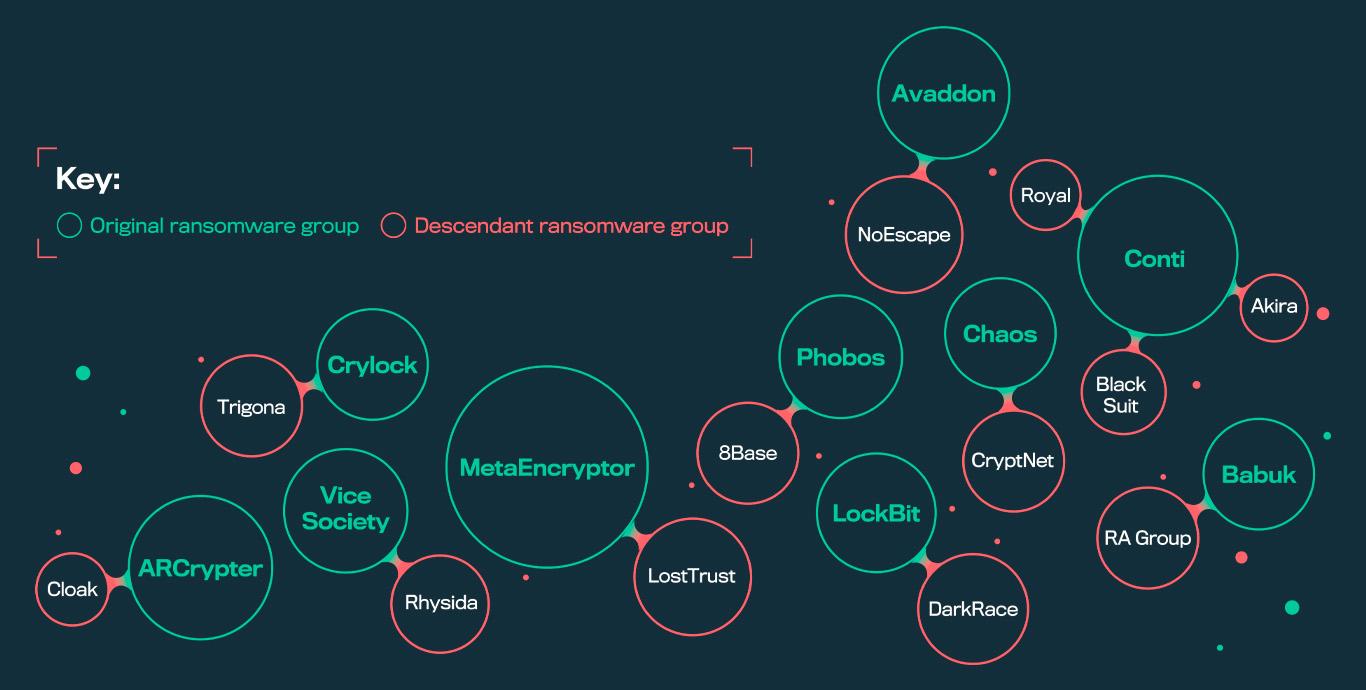
What channel does a ransomware attack come through?
Ransomware attacks employ diverse channels for delivery, with phishing emails being one of the most prevalent methods where cybercriminals use deceptive emails to distribute malware through malicious attachments or links.
Malicious websites and malvertising are additional vectors, exploiting vulnerabilities in web browsers or plugins to infect users who visit compromised sites. Remote Desktop Protocol (RDP) attacks target weak or default passwords on systems with exposed RDP, enabling unauthorized access and ransomware deployment. Drive-by downloads can occur when users visit compromised websites, initiating malware downloads, even without interaction. In addition, ransomware can be distributed via social engineering whereby a user can be tricked into clicking on a malicious link or downloading malicious software.
How can endpoints and end users be protected from Ransomware attacks?
Join our mailing list
Subcribe to our news and updates from WithSecure ans acquire valuable insights directly from our industry-leading professionals.








