Effective ransomware prevention: Insights from the Conti Playbook
Introduction
Our customers regularly ask us what more they can do to prevent ransomware outbreaks. Our experience has shown us that the correct way to counter cyber attacks is a solid, step-by-step detection and response (D&R) foundation. Recently we’ve had the opportunity to look at this from the perspective of attackers, thanks to a massive leak of inside information and data from one of the big Ransomware as a Service (RaaS) groups: Conti.
Who is the Conti group?
Conti is a ransomware group of Russian and Eastern European cyber criminals operating like a standard technology company. The Conti group was responsible for many high-profile ransomware outbreaks and recently pledged its allegiance to the Russian state following the invasion of Ukraine. In 2021 and 2022, documents and top-secret information pertaining to the group were leaked by a Ukrainian affiliate.
The Conti group licenses its tooling, infrastructure, and training to affiliates for a share of their profits, and it is through these affiliates that cyber security teams have been able to gather a significant amount of information about how Conti operates.
Why should we be interested?
The Conti leaks provide a glimpse into how larger threat groups operate, including what Conti’s tools, techniques and procedures (TTPs) look like. The information included in the Conti leaks can help us transform our abstract perception of ransomware incidents into simpler and more realistic attack paths that we can follow and build detections for.
What does their Playbook show?
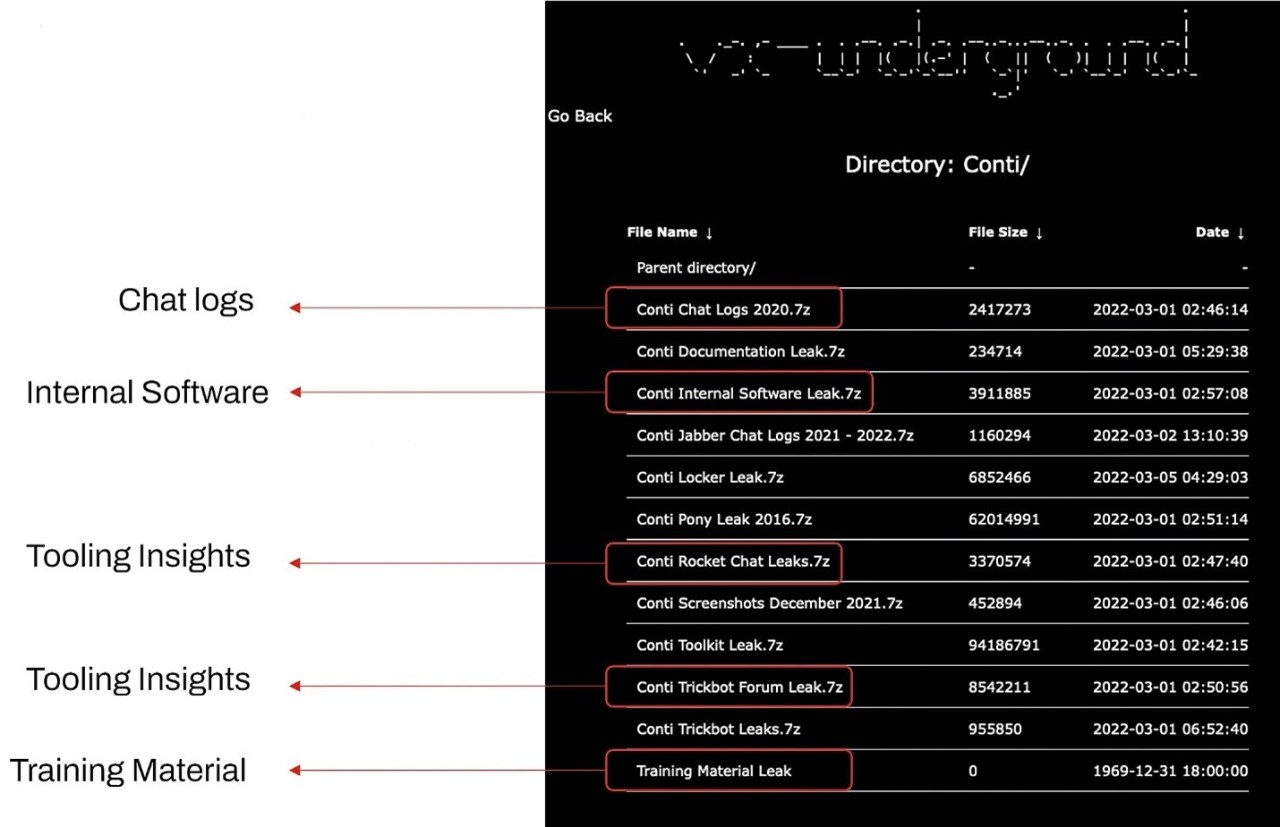
Figure 1: 7zip archives containing the contents of the Conti Leak.
Figure 1 shows the site where the contents of the leak are stored. The chat logs display the resources used by Conti and their affiliates, including the companies they target, types of vulnerabilities they use, their preferred hacking techniques, and even the times of day that they choose to operate.
The internal software and tooling insights (Rocket.Chat and TrickBot) utilized by Conti are readily available materials often used by penetration testers and provide a glimpse into how Conti operates internally.
Lastly, the training material file indicates Conti’s operator skill level and can help defense teams to determine the operation’s level of complexity.
Training regime
A lot of the training materials used by Conti include familiar software names such as Metasploit and Cobalt Strike: Again, these are not always associated with high-skilled acts. Any security defense organization should either already have or be able to develop detection and response strategies for incidents where such tooling may have been used.
Technical skill
Conti’s use of simple payload types, such as the generation of the MSFVenom command, is one clear indication the group use open-source tooling for which we can build detections, not custom tradecraft. Several payload-type errors are obvious; the attackers use codes like the Bind TCP Shellcode to gain remote access, as well as port 4444 (a commonly related attack port) and file names such as bindshell64.dll. Some of these are easy to detect, even without sophisticated detection tools.
Tools, techniques and procedures
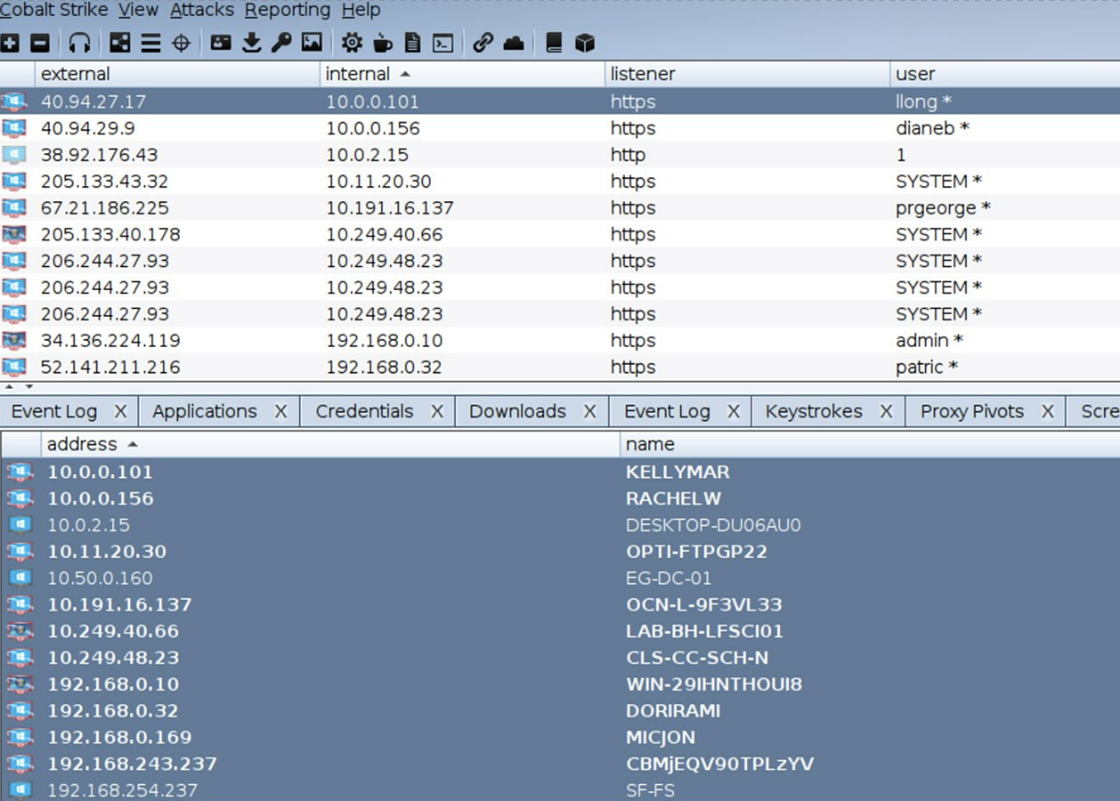
Figure 2: Cobalt Strike team server.
Figure 2 shows an access point which allows attackers to view the machines they are trying to hack.
The tools and techniques appearing most frequently within the Conti leaks are:
- Cobalt Strike
- PowerView
- Metasploit
- ShareFinder
- AnyDesk
- Mimikatz.
Kill chain detection opportunities
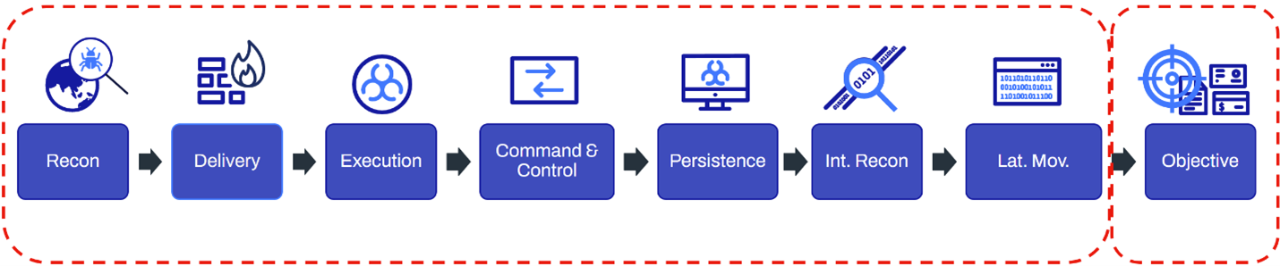
Figure 3: WithSecure™ kill chain.
If defense teams can effectively detect Conti’s TTPs at the first seven stages of the kill chain shown in figure 3, successful prevention of a ransomware outbreak would be guaranteed.
- improving security hygiene by reducing the attack surface
- implementing protection, detection and response.
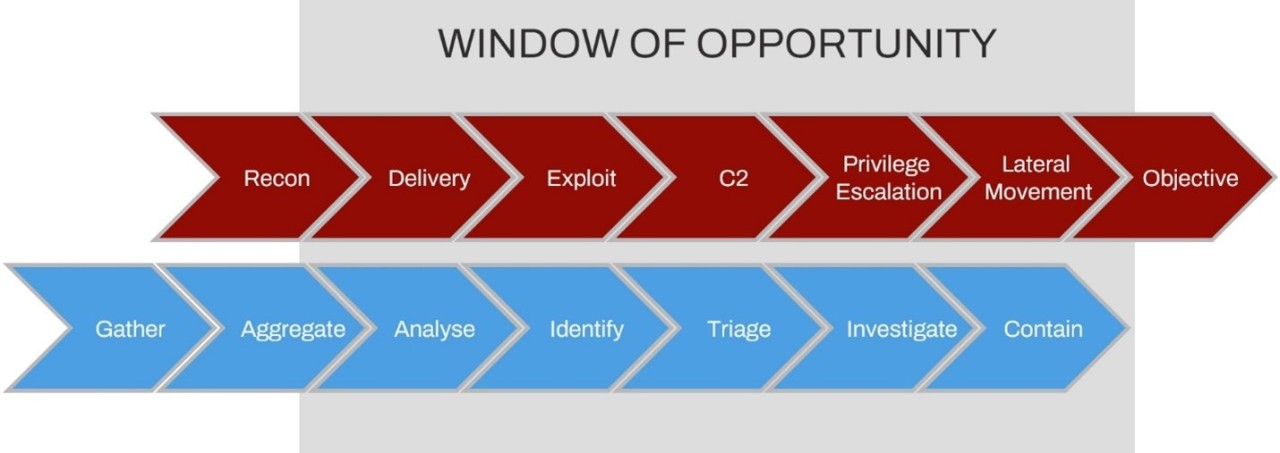
Figure 4: Red team kill chain (above) and blue team kill chain (below).
The diagram in Figure 4 breaks down the D&R concept introduced by Microsoft. The red portion of the diagram represents the attack kill chain: the blue portion represents the defense kill chain.
The identification, triage, investigation, and containment steps are particularly crucial. Defense teams need these to successfully evict any presence of ransomware actors. Hence, trustworthy and capable Detection & Response services are crucial to ensuring all these steps are followed.
Deep dive: TTPs (Tools, techniques, and procedures)
Some of the TTPs included in the Conti leaks involve phishing and targeting well-known vulnerabilities:
Gaining access
Phishing: TrickBot payload via email
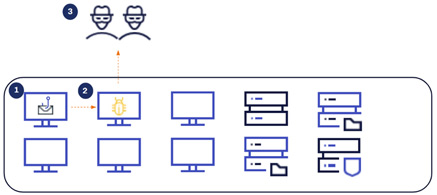
Figure 5.1: TrickBot via phishing emails.
Conti have recently taken over (1) TrickBot Malware. Their intent is to send large numbers of phishing emails to increase the chances of someone executing the payload. TrickBot can then deploy (2) Cobalt Strike, which then leads to (3) C2 activity (command and control infrastructure) so that the attackers can gain access to a machine within the environment.
Targeting well-known vulnerabilities: Vulnerable FortiGate Firewall
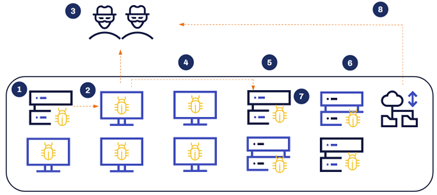
Figure 5.2: Deployment of ransomware via vulnerable FortiGate Firewalls
Conti have been known to target vulnerable FortiGate Firewalls. Once they gain initial access, they can deploy Cobalt Strike and gain control over a workstation or server within the target organization, just like with the phishing technique.
After gaining access
Next, the attacker can implement a form of (4) internal reconnaissance. This can be fulfilled by utilizing binaries that are already on disk, such as an NLTest, which can be used to list domain controllers on the domain; or netgroup, which is used for gathering information about certain groups, specifically domain administrators. The command AdFind is also frequently used.
Once this information has been collected, the attackers will try to escalate their privileges using techniques such as (5) Kerberoasting to find SPN (service principal name) accounts with weak passwords and high privileges.. They will then pursue the Active Directory environment through a technique called (6) DCSync. By this point, the domain is fully comprised, the contents of the Active Directory have been leaked, and the attackers have access to the most important accounts throughout the domain. (7) NTDSutil provides a similar output as DCSync.
Finally, (8) Rclone is an example of an open-source tool used by Conti to exfiltrate data. Once this is achieved, the deployment of ransomware and, in some cases, extortion, can begin.
Detection opportunities
How to detect Conti TTPs
There are several detection opportunities for each of the Conti attack stages explained above.
Problem: TrickBot payload email/Vulnerable Fortigate Firewall
Solution: Patch.Patching vulnerabilities is the only real way to prevent them from being exploited and to mitigate a ransomware attack. A dedicated phishing training program to educate server users is also valuable.
Problem: Cobalt Strike payload deployed
Solution: Cobalt Strike Beacon Payload DetectionThree key techniques for detecting Cobalt Strike are:
- DLL references to ‘beacon.dll’ or ‘beacon.x64.dll’ – the word ‘beacon’ is often heavily associated with Cobalt Strike.
- Memory artifacts – there are artifacts in running process memory which show process injection.
- Lateral movement techniques – Adversaries use lateral movement in Cobalt Strike activity to progress through the target network and move closer to valuable assets. There are tools and techniques you can use to detect this type of activity.
Problem: Cobalt Strike C2 activity
Solution: Cobalt Strike C2 pathsCobalt Strike uses a selection of default URI paths for its C2 communications:
- You can create detections for traffic to these paths – These may not be the most reliable of detections, but if your security organization or team can conduct a more thorough investigation, it could at least be the trigger point for further investigation.
- Review commonly used ‘malleable C2 profiles’ and create detections – These are customizable C2 profiles that can be utilized within Cobalt Strike and perform a very similar exercise to identify those URI paths most frequently seen.
Problem: Internal reconnaissance
Solution: Internal reconnaissance detection
Hunt for these signs of unusual activity:
- If AdFind is not used in your environment as part of your standard business operations, track possible instances where it is utilized with command line parameters containing passwords, as this is suspicious activity that will require further investigation.
- If you see NLTest with the arguments DCList being used to track domain controllers or attempts being made to map the domain admins group, these are also sure-fire signs you have a keen malicious intruder at hand.
- Look for enumeration commands when they originate from an injected process: When Cobalt Strike exploits a running process, you will see memory artifacts. If that same running process is executing these commands, then a thorough investigation is in order.
Problem: Kerberoasting
Solution: Kerberoasting detectionKerberoasting can be detected in several ways:
- Look for the process name powershell.exe with arguments containing “kerberoast”.
- Search for EventId. 4769 is an EventId associated with kerberoast service ticket requests. If the frequency of these requests is particularly large and they’re coming from a user who does not usually carry out such activity, this would call for an investigation.
Problems: DCSync and Ntdsutil
Solution(s):
- The commands DCSync and Ntdsutil are equally used to collect as much information as possible regarding the targeted Active Directory. Detection for both can be built in the following ways (using DCSync first as a primary example):
Event ID 4662 with property DS-Replication-Get-Changes-All, DS-Replication-Get-Changes-In-Filtered-Set – DCSync generates an event ID (4662) on the domain controller which can be detected, especially when it carries unique properties associated with DS replication.
From account not associated with DC replication – Through process data, we can easily identify Ntdsutil when an adversary is making attempts to export copies of active directory. Look for commands with arguments containing “ifm” and “create”.
Problem: Rclone exfiltration
Solution: Look for instances of rclone in process and network logs.
Sound prevention
Other steps:
- Plot published TTPs and test in Purple Team manner to ensure coverage – The detection mechanisms listed in this article are replicable, and can be used to detect and mitigate any risk associated with Conti or a similar type of threat group.
- Use Red Teams to ensure your Detection and Response works properly – Red Teamers work at an impressively advanced level and are the best form of simulation. If your organization’s security service can detect capable red teams, you can be fairly confident that most adversaries will be caught as well.
- Assess behaviors – Create detections by looking for the underlying activity: the behaviors that would be replicated by multiple tools or techniques.
- Suppress external attack paths – Please patch. This is the easiest way to ensure a threat does not make its way into the environment through the externally facing assets.
Conclusion
A ransomware attack can only be defeated with a solid Detection and Response strategy. If D&R teams can effectively investigate each attack path in their estate using the appropriate defense tools, techniques, and procedures at the first and most crucial stages of the kill chain, any malicious activities will be successfully foiled before they can lead to a full-blown ransomware attack.
This article was adapted from a presentation given by Arran Purewal. Watch the full talk here.