Ransomware profits are transforming cyber crime
To say that ransomware is a thorn in the side of organizations across the globe is an understatement.
Since its initial appearance over 30 years ago, it’s grown from one type of malware among many to become synonymous with the online extortion model of cyber crime. Ransoms have grown in tandem, from charging individuals hundreds of dollars to access family photos or documents, to charging multi-national organizations millions of dollars to restore their IT infrastructure.
A new report published by WithSecure found that the huge profits of ransomware have led to a rapid evolution and professionalization of the wider cybercrime industry, and the rapid growth of a supporting underground marketplace of products and service providers. In many ways, the cyber crime ecosystem mirrors the increasingly service-oriented tech industry, where different parts of a single operation are outsourced to specialized “as-a-service” providers.
Given ransomware groups’ integral role in driving this trend, it is worth organizations’ time to understand their exposure to ransomware and the impact these attacks have.
Extortion is the new black
The ransomware landscape has evolved since its origins in 1989 and the financially motivated cyber criminals who engage in it are best described as falling into one of three categories:
- Singular point of extortion groups, who use ransomware to encrypt a target’s systems, but do not operate a data leak platform. These actors demand ransom in return for a decryptor.
- Multi-point of extortion groups, who use ransomware/destructive techniques to hinder a target’s operations, but also steal data and further extort the organization through the threat of leaking data on the dark web. These actors demand ransom in return for a decryptor/return of data and to stop the leaking of data. This can either be a single payment, or separate payments.
- Data extortion groups, who do not run a typical ransomware group, but who simply engage in the theft of data and the subsequent threat of leaking that data if a ransom is not paid. No data destruction or encryption typically takes place.
Singular point of extortion groups actually make up the majority of ransomware attacks in the landscape. The attack is simpler, does not require large infrastructure, and can be undertaken with little resources, which is why they are more common.
Multi-point of extortion groups are the ones you will often hear about in the media and often feature in reporting. These groups have also been responsible for some of the most high-profile attacks and have demanded vast sums of money as part of their attacks, such as those perpetrated by the now-defunct Conti and REvil groups. These groups self-advertise their crimes through their leak sites on the dark web, making it easier to track their activities. It’s important to note, however, that this is still just a glimpse into the full extent of the landscape, as we only see some of the victims, as those who pay without delay may never appear on leak sites.
Many argue that data extortion groups should not be included in the ransomware landscape, and we would be inclined to agree. After all, if the attack doesn’t involve the use of some sort of tool to encrypt/destroy data, is it ransomware? The issue with this is the close relationship between many data theft actors and other ransomware groups. Karakurt, for example, is a known spin-off group from Conti who’s infrastructure and tactics, techniques, and procedures (TTPs) overlap heavily with ransomware groups.
The following statistics are an analysis of data leaks taken from multi-point of extortion groups and data extortion groups who operate leak sites. We acknowledge that this only allows insight into a small proportion of the ransomware landscape. However, we believe it still provides value as the singular point of extortion groups and other actors will likely follow the same trends.
In summary:
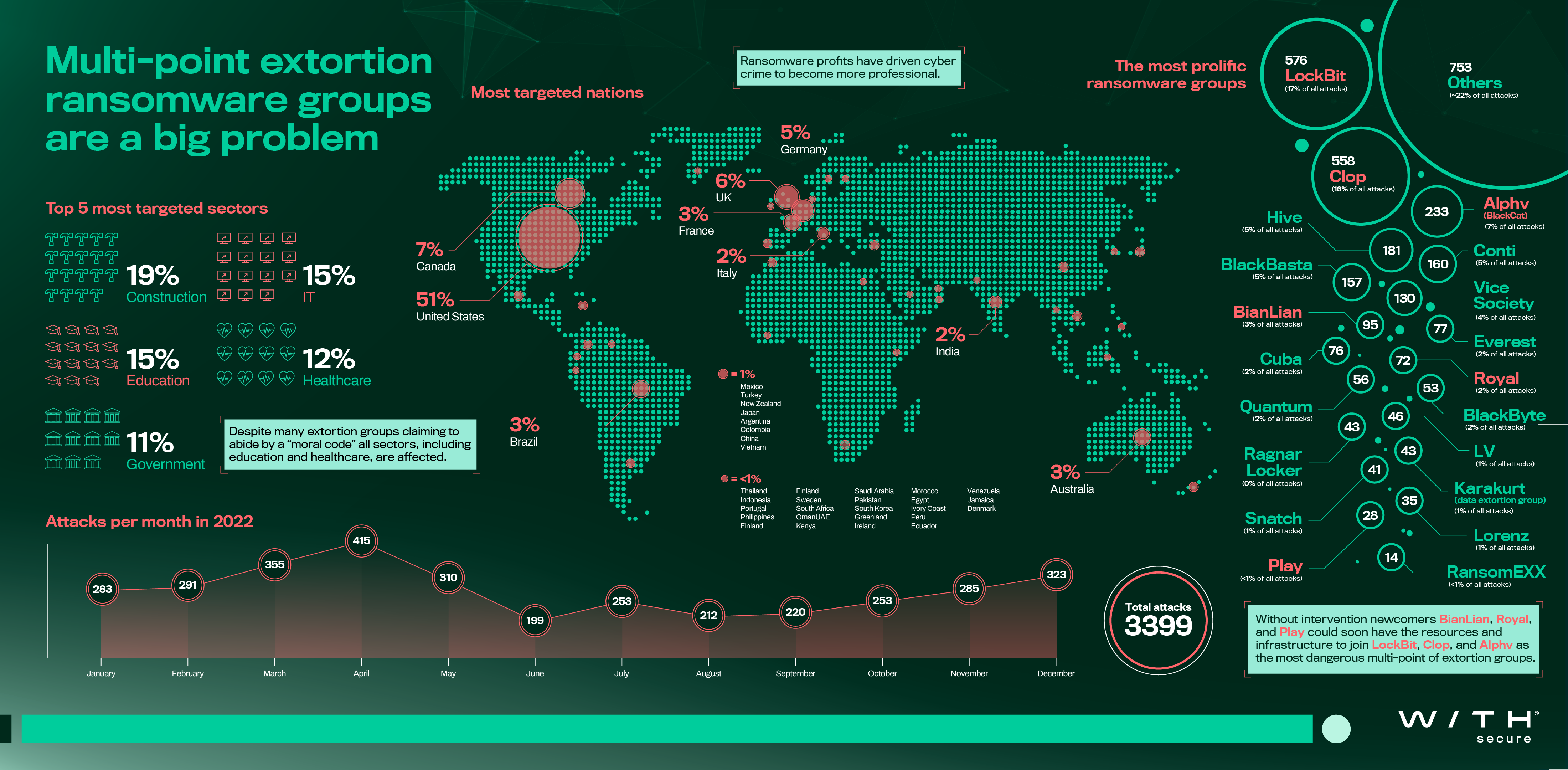
- LockBit, Clop, and Alphv were the most prevalent multi-point of extortion groups in the ransomware landscape.
- Newcomers BianLian, Royal, and Play appear to have the resources, infrastructure, and ability to become dominant figures in the landscape, without intervention. It is also noteworthy to mention that new groups should not be understood as inexperienced groups. New groups may consist of very professional criminals with years or even decades of cyber crime experience.
- The most targeted nation was the United States of America (51% of all attacks).
- While the construction sector was the most affected sector in 2022, all sectors were targeted, including the education and healthcare sectors, despite many extortion groups claiming to abide by a “moral code” that prevents this.
Cyber crime-as-a-service was born out of RaaS’ success
Many major ransomware groups are operating a service provider, ransomware-as-a-service (RaaS) model where they supply tooling and expertise to affiliates, and in return take a cut of the profits. As well as the professionalization of the root ransomware industry, these profits have also driven the rapid development of a service industry providing all the tools and services that an up-and-coming threat group could need. And thanks to cryptocurrency and dark web routing services, the many different groups involved are able to anonymously buy and sell services, and access their profits.
Impacting ransomware profits has almost certainly been a strategic goal for organizations seeking to disrupt actors. While cyber insurance policies have driven positive change, ultimately they do also fund some elements of cybercrime. Authorities had some success in this area with sanctions against organizations, making it unlawful to pay certain ransoms. We can expect this to continue throughout 2023 as ransomware gets increasingly recognized as a top tier threat.
The growing professionalization of cyber crime and what you can do
If you’d like to hear more about the professionalization of cyber crime, you can read our new report, or watch the recording of our latest webinar.