The Critical Role of Attack Path Mapping in Exposure Management

In today’s rapidly evolving threat landscape, simply identifying vulnerabilities isn’t enough.
Security teams must understand how these weaknesses connect - how they could be chained together by an attacker to reach critical systems or data. This is where attack path mapping plays a crucial role. By visualizing how an attacker might move through an environment - leveraging misconfigurations, exposed services, and identity relationships - organizations can proactively uncover and address the most dangerous routes before they are exploited.
Moving Beyond Traditional Risk Assessments
Traditional vulnerability management typically evaluates risks in isolation, using static scores based on severity or asset criticality. While these methods provide value, they overlook a key fact: attackers don’t think in Common Vulnerabilites and Exposures (CVEs) - they think in paths. Adversaries look for ways to move laterally, escalate privileges, and chain together opportunities to achieve their goals.
At the same time, the sheer volume of vulnerabilities and misconfigurations identified in most environments can be overwhelming. Security teams are often left asking: “Which issues actually matter most?” Attack path mapping answers this question by placing each finding in context. It reveals how individual weaknesses can be combined to form real, exploitable attack chains - allowing teams to cut through the noise and focus on those that present a genuine route to compromise. This context-driven approach helps prioritize what truly matters - not just what is vulnerable, but how it could be used in a broader attack scenario.
How WithSecure’s Attack Path Mapping Works in Practice
At WithSecure, attack path mapping is grounded in a practical understanding of attacker behavior - augmented by artificial intelligence. Our approach begins by evaluating all likely entry points into the environment. This includes traditional vectors such as internet-facing services and vulnerable software, but also modern attack scenarios like phishing. In these cases, we assess the value and exposure of individual users or their devices, recognizing that the human element is often the first link in the chain.
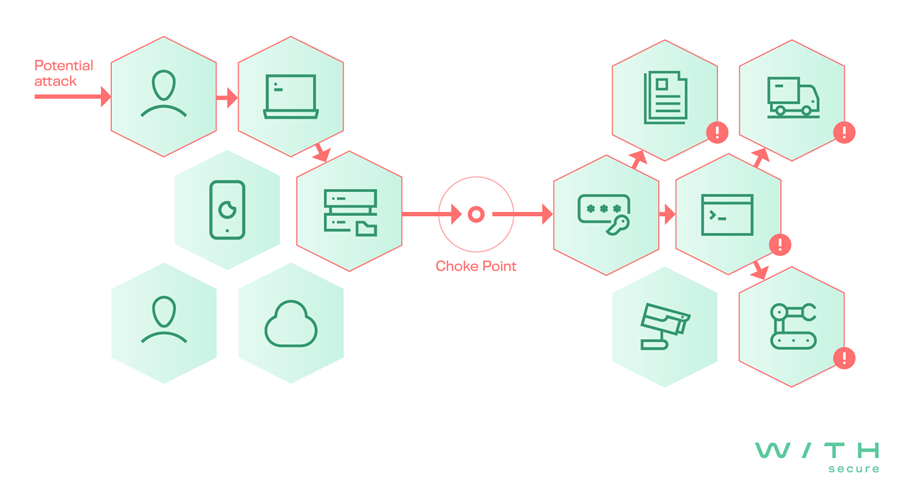
What makes our approach truly unique is the use of an AI-driven simulation engine, built on a patent-pending algorithm designed to mirror realistic adversary behavior. The engine automatically builds a model of the organization’s infrastructure and simulates potential attack paths from the perspective of a motivated attacker. This enables rapid, scalable analysis that adapts as the environment evolves.
Safe and Non-Intrusive by Design
Importantly, our attack path mapping is completely non-intrusive. It is a safe simulation that models adversary behavior without executing any potentially harmful activities. Unlike penetration testing, which can introduce operational risk, our method avoids disruption by relying on observed data, contextual analysis, and secure modeling techniques. Organizations gain deep insight into their exposure - without touching production systems or requiring elevated access.
Simulating Attacker Logic - Not Just Risk Scores
Once potential access points are identified, we simulate the logical progression of an attacker. We attempt to “walk through” each step - exploiting local vulnerabilities, performing lateral movements, and escalating privileges - through modelling, not execution. Each step is analyzed in detail, based on real attacker Tactics, Techniques, and Procedures (TTPs), with an emphasis on what conditions must be met - such as credentials, access levels, or network reachability.
What sets WithSecure apart is how we model attacker motivation and gains at each step. Our system doesn’t just identify possible moves; it evaluates how beneficial each action would be to an attacker. This includes assessing how much control they gain, what sensitive data becomes accessible, and how likely they are to succeed. This deeper understanding allows us to score and prioritize attack paths based on both their feasibility and their strategic value to an adversary.
Just as importantly, our simulations help identify choke points - key nodes or conditions that appear in multiple attack paths and enable significant attacker progress. These may be powerful accounts, overexposed systems, or misconfigurations that act as enablers for lateral movement or privilege escalation. Remediating such choke points is often one of the most efficient and high-impact actions a security team can take. Fixing a single weak link can neutralize multiple attack chains at once, dramatically reducing overall exposure with minimal effort.
Leveraging Integrated Visibility and Controls
Organizations that use WithSecure Endpoint Detection and Response solution with response actions enabled benefit from even greater accuracy. Our platform validates whether lateral movement is technically possible by checking network connectivity between devices. This helps eliminate false positives and highlights only the viable paths an attacker could take.
We also integrate with WithSecure Elements Exposure Management for Cloud, combining endpoint data, user behavior, privilege levels, and cloud misconfigurations. This broad visibility enables us to identify advanced attack scenarios such as data theft, cryptomining, and ransomware spread - including those that cross from on-premises systems into cloud environments. The result is a unified view of exposure across the entire digital estate.
Enabling Proactive Exposure Management
Attack path mapping turns exposure management from a reactive, checklist-driven process into a proactive, intelligence-led strategy. By continuously modeling and analyzing attack routes, security teams can take action before threats materialize. This includes focusing on high-impact choke points, reducing lateral movement potential, and strengthening key defenses.
The benefits extend beyond technical teams. By providing a clear, visual representation of organizational exposure, attack path mapping aligns IT, security, and risk functions around a common understanding of what needs to be protected - and why it needs protecting. This collaboration accelerates decision-making and ensures that security investments deliver maximum impact.
WithSecure™ Elements Exposure Management
Transform your cybersecurity strategy with our Elements Exposure Management. Predict and prevent breaches with advanced, AI-driven visibility and control. Start defending smarter today!
Read more