Raising Your Cyber Security Maturity: Where Do You Stand?

Why a Cyber Security Checklist Matters More Than Ever
Cyber security is not just a purely technical issue – it’s a business-critical challenge. Breaches, ransomware, and data leaks can disrupt operations and erode customer trust overnight. Yet, many organizations still stumble on the same basic pitfalls that attackers are quick to exploit.
A cyber security checklist provides a practical way to evaluate your organization’s readiness. It helps you understand whether the fundamentals are in place, where the weak spots are, and how to prioritize improvements.
Cyber Security Hygiene: Getting the Basics Right
Cyber hygiene refers to the day-to-day practices that prevent the most common and opportunistic attacks:
Applying software patches and updates on time
Enforcing strong, multi-factor authentication
Managing user accounts and access rights carefully
Keeping reliable backups and tested recovery plans
Providing security awareness training to employees
These practices may not make headlines, but neglecting them often opens the door to serious breaches. A checklist helps ensure that these basics are consistently applied across the organization.
But hygiene alone isn’t enough. An organization must grow its security maturity and strengthen resilience—the ability to detect and respond to attacks quickly, and to recover as efficiently as possible. In practice, this means developing Detection & Response capabilities and ensuring robust recovery in critical situations.
Maturity: From Ad-Hoc to Systematic Security
Beyond hygiene, every organization should assess its security maturity. Maturity reflects how structured and proactive your approach is:
Is security still reactive – fixes happen only after something goes wrong?
Or is it embedded in processes, assessed regularly, and continuously improved?
The WithSecure checklist lets you benchmark your current maturity level and identify the next steps. It turns isolated activities into a continuous, measurable program and is structured around four pillars:
- Foundations – get the basics right
- Visibility and response
- Hardening and deepened monitoring
- Testing and certification
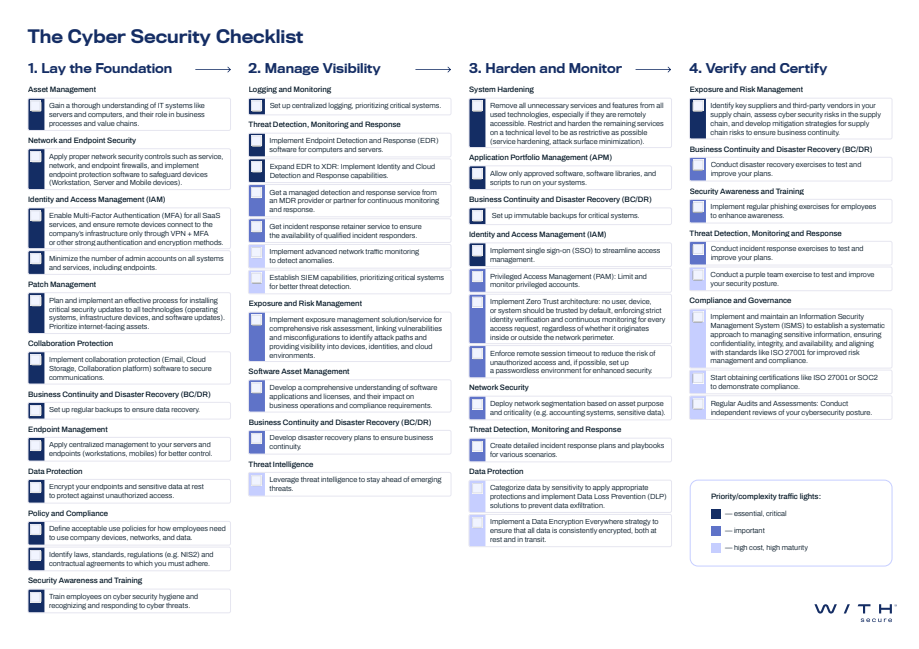
Across these pillars there are 42 concrete action boxes. Each box uses traffic-light indicators that show at a glance:
Cost/Effort (time and budget impact)
Maturity impact (how much the action raises your maturity)
This helps you quickly spot quick wins (low cost, high impact) and strategic investments (higher effort, significant maturity leap) within each pillar – moving the organization from a reactive model to a higher, systematic maturity.
Why Small Gaps Matter
A crucial point often overlooked is the importance of small gaps. Even when most areas are covered, one overlooked misconfiguration, outdated application, or overly permissive account can become the critical entry point an attacker needs.
Think of it like a small crack in a dam – it might seem insignificant at first, but under pressure it can cause a major breach. Attackers thrive on chaining together small oversights into a path that leads to valuable systems and data. A checklist makes these gaps visible before they can be exploited.
The Benefits of a Checklist
A comprehensive checklist provides:
A quick snapshot of your current cyber security posture
Clarity on which issues truly need attention first
A common framework that works across industries and geographies
An easy way to align IT, security, and leadership on next steps
Most importantly, it allows you to turn vague concerns into concrete, actionable priorities.
Take the First Step
Improving cyber security doesn’t allways mean expensive tools or complex projects. It starts with ensuring the fundamentals are in place and identifying where small gaps might exist.
Download the WithSecure Cyber Security Checklist and take the first step toward stronger cyber hygiene and higher maturity.
WithSecure Cyber Security Checklist
WithSecure presents a comprehensive checklist, developed through collaboration with experts from multiple fields. This unique list provides a broad and unparalleled perspective on cyber security, organizing tasks by both priority and complexity. The checklist is specifically designed to help organizations protect their environments.
Download