Decode cyber security priorities for Management and Board
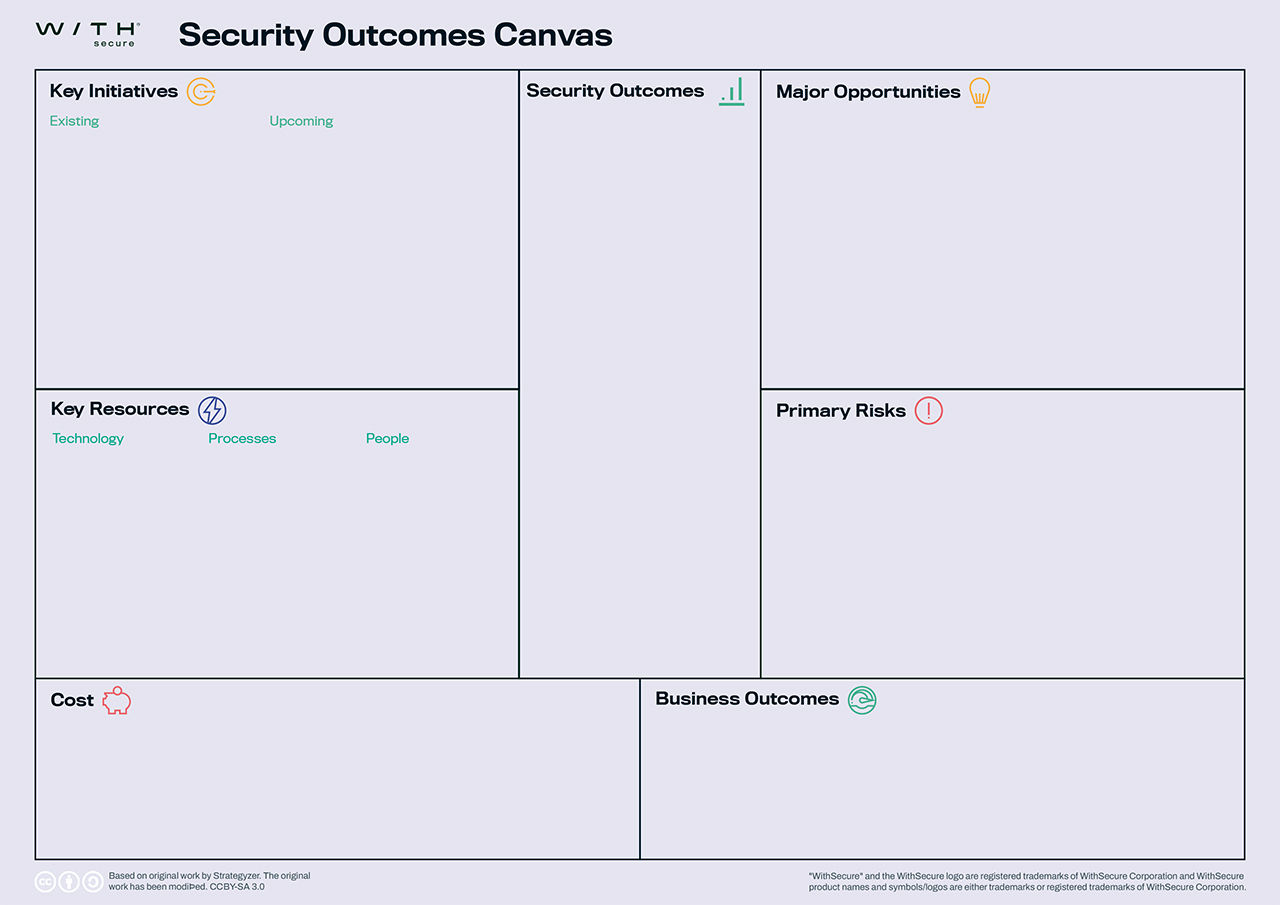
The Security Outcome Canvas is tool for organizations seeking clarity on aligning their security and business objectives.
The core areas
Business Outcomes
What business outcomes does your organization intend to have?
Primary Risks
What are the major risks to the business outcomes that will be addressed by these security outcomes?
Security Outcomes
What baseline security outcomes are needed by the organization? What security outcomes are needed to support the relevant business outcomes the organization desires?
Major Opportunities
What opportunities do you have in your organization that support our security outcomes?
Key Initiatives
Existing: What initiatives are already available to achieve these security outcomes?
Upcoming: What initiatives do we still need to do to achieve these security outcomes?
Key Resources
Technology: What technologies are already supporting these outcomes? What technologies are already available but not utilized for these outcomes? What new technologies are needed?
Processes: What existing processes are already supporting these outcomes? What new processes are needed? What processes will need to be modified?
People: Who are working on the existing initiatives? Who will be working on the upcoming initiatives?
Cost
What are the most important costs needed to achieve these security outcomes? Which initiatives are the most expensive?
Challenges and opportunities on Security Outcomes
Christine Bejerasco, Chief Information Security Officer at WithSecure, was on stage at SPHERE23 to introduce the Security Outcome Canvas – a new tool to help organizations better understand how to align their security and business goals.
How to fill canvas?
Identify and agree on the business outcomes that your organization intends to have.
For example:
- Increased credibility in our industry
- No material downtime of services
- High customer satisfaction
Identify the risks to those business outcomes.
For example:
- Supply chain attack to downstream partners/customers
- Data leaks
- Loss of infrastructure control
- Service interruptions
Define the security outcomes that can reduce the risk or increase the chances of success of these business outcomes.
For example:
- Increased cyber security mindshare everywhere
- Cyber security accountability is shifted left
- Built-in cyber security
Identify major opportunities that could help attain those security outcomes.
For example:
- IT cloudification
- Finance process revamp
Identify the existing and needed initiatives for these security outcomes.
For example:
- Existing
- External audits
- Incident governance
- Upcoming
- DevSecOps implementation
- SaaS-ification of applications
Identify the existing and needed resources for these security outcomes.
For example:
- Technology
- Cloud Protection for Salesforce/M365
- Cyber awareness training platform
- Processes
- Invoicing
- Vendor Management
- People
- External auditors
- CISO Office
- Enterprise IT
- Managed Detection & Response (MDR)
Define the cost and cost structures of the above initiatives and resources.
For example:
- External consultant fees
- CISO Office salaries
- DR Service subscription
- Training platform subscription
Want to talk in more detail?
Complete the form, and we'll be in touch as soon as possible.
What are Security Outcomes?
Most businesses stumble from one cyber security crisis to another. It’s hardly surprising: as security budgets continue to grow in the face of threats, security leaders must constantly justify the needed to defeat these threats.
In a Forrester study conducted on behalf of WithSecure, 60% of security decision-makers said they were in reactive mode and failing when it came to cyber.
Escaping this cycle of reactive behavior, and improving visibility of threats beyond just an attack surface or network perimeter is vital to improving any organization’s cyber security. But even that is not enough.
Outcome based security steps beyond the immediate need to defend, and demonstrates how cyber security can help actively support the pursuit of organizational goals. The need is already clear and present: 83% of respondents in the same Forrester poll wanted to adopt outcome-based cyber security approaches.