5 phases of a cyber attack: The attacker’s view
Business Security

Cyber security is not something you do once and then you’re done. It is a continuous process that should be part of everything you do. However, no one has the resources to do everything perfectly. Thus, your goal should be constant improvement.
Improving starts with understanding the risks and the threat landscape. This means understanding your adversaries, their objectives, and how they carry out their attacks.
Let’s imagine a case where a company has been hit by a ransomware outbreak. The company is actually dealing with a financially motivated targeted attack, but ransomware is being used as a cover to hide the more targeted activities. The real target is the sensitive customer data.
So, what happens in each phase of the attack?
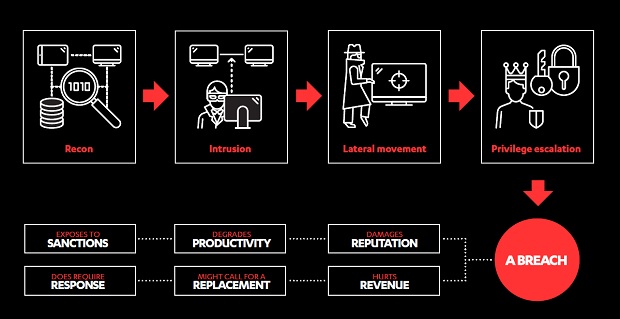
Phase 1: Recon
Timeline: months before detection
The attacker’s first goal is to identify potential targets for their mission. Attackers are often motivated by financial gain, access to sensitive information or damage to brand.
The attacker may collect information about the company from LinkedIn and the corporate website, map the supply chain, get building blueprints, information on security systems and available entry points. They may even visit the company building, an event or call the secretary. The attacker might set up a fake company, register domains and create fake profiles for social engineering purposes.
Once the attacker determines what defenses are in place, they choose their weapon. The selected vector is often impossible to prevent or detect. It can be a zero-day exploit, a spear-phishing campaign or bribing an employee. Usually there is a minimal business impact.
Finally, the attacker is ready to plan an avenue of attack.

Phase 2: Intrusion and presence
Timeline: months before detection
At the second phase of a cyber-attack, the attacker seeks to breach the corporate perimeter and gain a persistent foothold in the environment.
They may have spear-phished the company to gain credentials, used valid credentials to access the corporate infrastructure and downloaded more tools to access the environment. This is virtually untraceable.
It is very typical that the targeted organization is unable to detect or respond to the attack. Even if detected, it is impossible to deduce that our organization was the ultimate target. In practice, the attacker is always successful.
The initial intrusion is expanded to persistent, long-term, remote access to the company’s environment.
Phase 3: Lateral movement
Timeline: months or weeks before detection
Once the attacker has established a connection to the internal network, they seek to compromise additional systems and user accounts. Their goal is to expand the foothold and identify the systems housing the target data.
The attacker searches file servers to locate password files and other sensitive data, and maps the network to identify the target environment.
The attacker is often impersonating an authorized user. Therefore it is very difficult to spot the intruder in this phase.

Phase 4: Privilege escalation
Timeline: weeks or days before detection
The attacker seeks to identify and gain the necessary level of privilege to achieve their objectives. They have control over access channels and credentials acquired in the previous phases.
Finally the attacker gains access to the target data. Mail servers, document management systems and customer data are compromised.

Phase 5: Complete mission
Timeline: day 0
The attacker reaches the final stage of their mission. They exfiltrate the customer data they were after, corrupt critical systems and disrupt business operations. Then they destroy all evidence with ransomware.
The cost to the company rises exponentially if the attack is not defeated.
In this example the target was reached before detection. This is typical. Data breaches are extremely difficult to detect, because attackers use common tools and legitimate credentials.
That’s why you need to stay alert at all times. With cyber security, you are never done.
This fictional example is based on experience from real-life cases and experience of our ethical hackers. WithSecure Red Team test is an eye-opening exercise, where the defensive capabilities of companies are tested using the same model the real hackers use.
Check out this video about red teaming:
Related Posts

- Blog post
- Catarina de Faria Cristas
- 2022
- Detect and respond to attacks
A closer look at Flubot's DoH tunneling
Flubot is an Android banking trojan, first seen in December 2020, which has gained traction in 2021 and compromised a huge number of devices worldwide, including significant incidents in Spain and Finland.
Read more
- Blog post
- 2017
- Melissa Michael
- Attack Surface Management
- IoT
- Protect and prevent threats
Of Cameras & Compromise: How IoT Could Dull Your Competitive Edge
The Internet of Things is here. And with it are exciting possibilities, cost savings and efficiencies. But there’s a dark side to this bright new world, and it can be summed up in what we call Hypponen’s Law: If it’s smart, it’s vulnerable.
Read more
- Blog post
- Noora Hyvärinen
- 2018
- Python
- Protect and prevent threats
How to decompile any Python binary
At WithSecure we often encounter binary payloads that are generated from compiled Python. These are usually generated with tools such as py2exe or PyInstaller to create a Windows executable.
Read more
- Blog post
- Adam Pilkey
- 2018
- Detect and respond to attacks
The Chilling Reality of Cold Boot Attacks
What do you do when you finish working with your laptop? Do you turn it off? Put it to sleep? Just close the lid and walk away?
Read more