Research Bulletin: Smart Padlocks
WithSecure Labs has published research detailing a former intern’s discovery of security issues with a line of smart padlocks, once again highlighting the challenges vendors and consumers face in securing internet-of-things (IoT) devices. According to the research, an attacker could exploit these issues to transfer ownership of the lock to themselves, giving full control of the lock to the attacker.
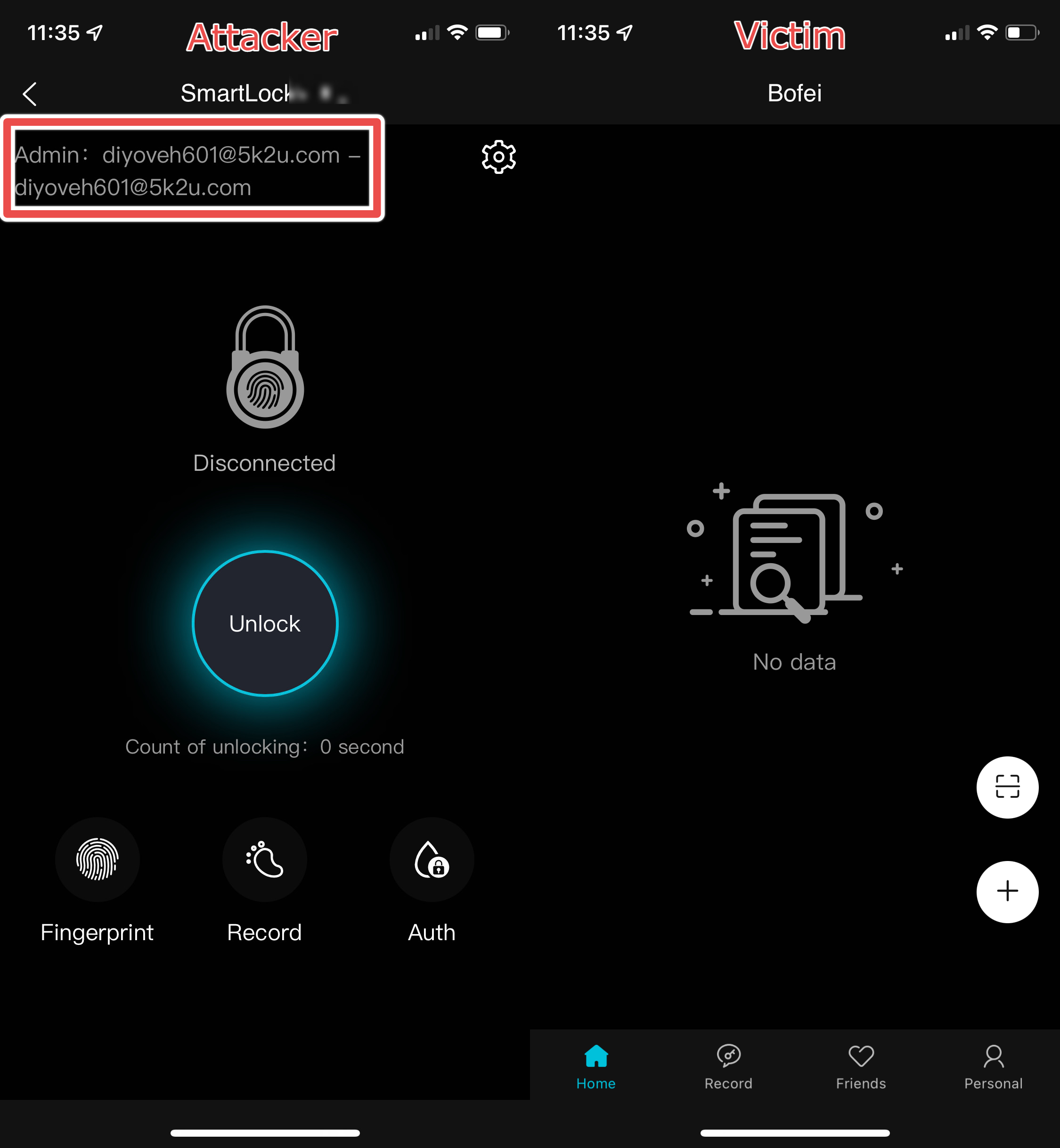
The locks, sold by Megafeis, are smart padlocks that users can unlock with their fingerprint, or a mobile app via Bluetooth.
Abdullah Ansari, the researcher who discovered the security issues while working as an intern at WithSecure™, was interested in learning more about hacking IoT devices. He decided to study smart locks and chose Megafeis’ FB50s Smart Padlock for his research.
According to his blog post , Abdullah was able to identify several issues that an attacker could use to take over a specific lock.
The specific vulnerabilities discovered by Abdullah are as follows:
- CVE-2022-45636 - Insecure Authorization Scheme for API Requests
- CVE-2022-45637 - Insecure Password Reset Code Expiry Mechanism
- CVE-2022-45634 - Lock Owner's Username Disclosure
- CVE-2022-45635 - Insecure Password Policy & Lack of Rate Limiting
By exploiting the use of an insecure authorization scheme with the API, Abdullah transferred ownership of the lock without permission, and then opened it. He was able to reproduce this attack against several other locks sold by Megafeis, which he demonstrates in this video:
As markets become flooded with inexpensive IoT devices, security has become a significant concern. Challenges faced by the business community, consumers, and regulators, have been well-documented. In fact, “If It’s Smart, It’s Vulnerable”, the name of a book written by WithSecure™ Chief Research Officer Mikko Hypponen, refers to Hypponen’s Law about IoT security.
Considering the growing popularity of IoT devices, as well as the difficulties in securing them and associated risks, research into securing smart devices is increasingly important for the cyber security industry.
Mitigation advice
In spite of making several attempts using a variety of channels, Abdullah and other WithSecure™ consultants were unable to establish contact with Megafeis to share the research and help them fix the problems. As per WithSecure Labs’ vulnerability disclosure policy, Abdullah and the researchers decided to publish the research after their unsuccessful attempts to reach Megafeis.
As WithSecure’s attempts to reach Megafeis were unsuccessful, the researchers are not aware of any fix for the problems Abdullah discovered as of the time this was published. Consequentially, current lock owners are advised to be aware of the weaknesses in Megafeis devices before using them to secure valuables or confidential material.