Unveiling the Arsenal: Exploring Attacker Toolsets and Tactics
Defenders are continually engaged in an intricate battle with cyber adversaries.
As organizations strengthen their defenses, attackers adapt, employing increasingly sophisticated toolsets to fly under the radar and achieve their objectives. Understanding these malicious toolsets and their distinct objectives is important in safeguarding against cyber threats.
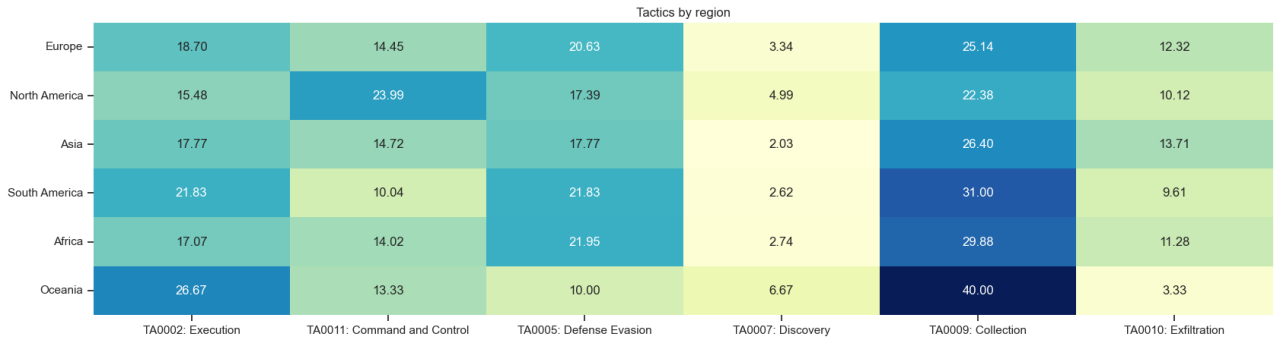
In this analysis, we highlight different paths attackers use to achieve their objectives. It is difficult for organizations to defend against every single threat in the ever-changing threat landscape. However, by looking at true positive trends, attacker’s toolsets, incident types and MITRE matrices from a particular region and relevant vertical, an organization can refine and test their defenses by prioritizing against the kind of attacks that can affect them the most.