DUCKTAIL: An infostealer malware targeting Facebook business accounts
WithSecure has discovered an ongoing operation (dubbed "DUCKTAIL") that targets individuals and organizations that operate on Facebook’s Business/Ads platform.
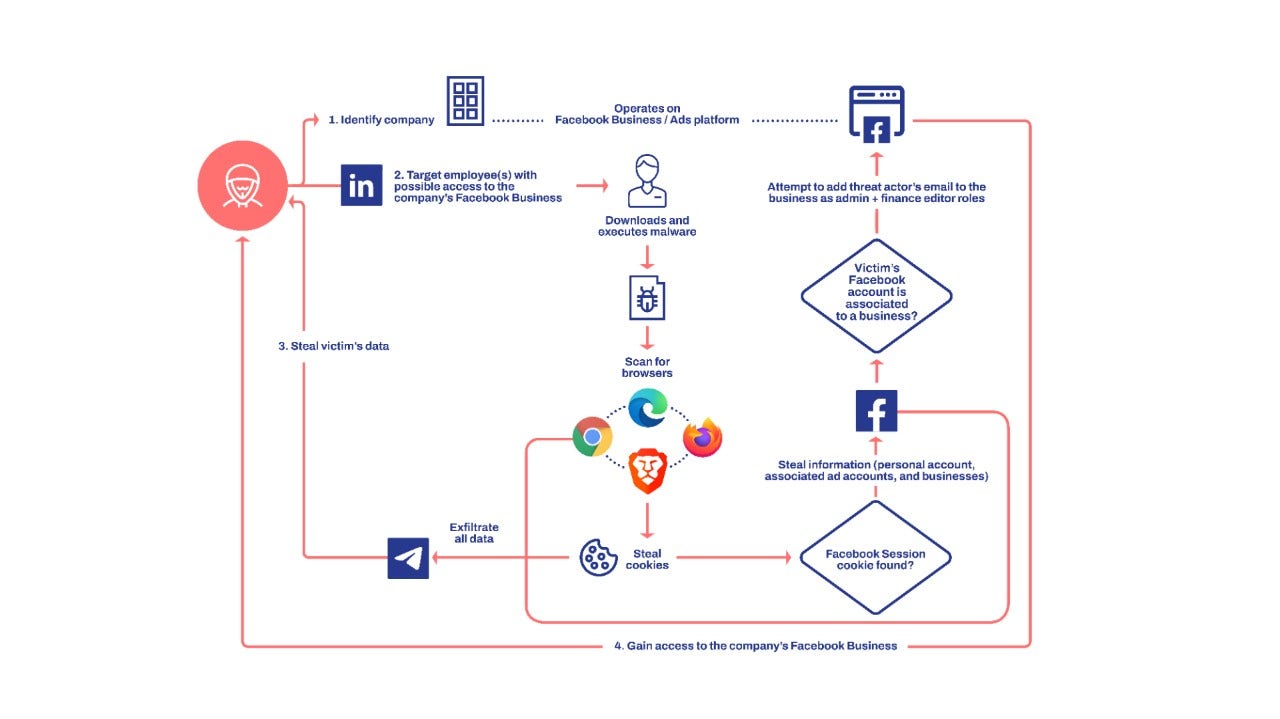
The threat actor targets individuals and employees that may have access to a Facebook Business account with an information-stealer malware. The malware is designed to steal browser cookies and take advantage of authenticated Facebook sessions to steal information from the victim's Facebook account and ultimately hijack any Facebook Business account that the victim has sufficient access to.
The hijacking is achieved by adding the threat actor's e-mail address to the Facebook Business account with Admin and Finance editor roles. In essence, this provides the threat actor unrestricted access to the account.
We have observed individuals with managerial, digital marketing, digital media, and human resources roles in companies to have been targeted. WithSecure has identified instances where the malware was delivered to victims through LinkedIn.
Based upon analysis and gathered data, we have determined that the operation is conducted by a Vietnamese threat actor. The chain of evidence suggests that the threat actor’s motives are financially driven.
The popularity of social network and media platforms remain on the rise, and we expect cybercriminals to be naturally drawn towards exploiting them however they can. We believe this trend will continue as cybercriminals increasingly abuse these platforms to achieve objectives including malware distribution, theft, disinformation campaigns, and fraud. Up until now, we’ve been relatively lucky – our most recent examples of social network-based cybercrime reveal threat actors using relatively mild motives (monetization). Future cybercriminal campaigns on social network platforms may not be so gentle.
A full report describing the timeline of DUCKTAIL’s activities, a detailed analysis of its malware component, and appendices containing indicators of compromise, Yara detection rules, metadata, and MITRE ATT&CK techniques can be downloaded from a link on this page.
Prevention
As with all operations of this nature, vigilance and alertness are key to avoiding becoming a victim. Many spear phishing campaigns target users on LinkedIn, and if you are in a role that has admin access to corporate social media accounts, it is important to exercise caution when interacting with others on social media platforms. It goes without saying that caution should also be exercised when dealing with attachments or links sent from individuals you are unfamiliar with.
Detection
WithSecure Elements Endpoint Detection and Response
WithSecure Elements Endpoint Detection and Response detects multiple stages of the attack lifecycle. This will generate a single incident with detailed detections, including:
Ducktail infostealer detected
File download headless browser
Dotnet telegram bot module load
Webbrowser database file accessed
Abnormal connection to telegram api
WithSecure Elements Endpoint Protection
WithSecure Elements Endpoint Protection offers multiple detections that detect the malware and its behavior. Ensure that real-time protection as well as DeepGuard are enabled. You may run a full scan on your endpoint. Our products currently offer the following detections against the malware:
Trojan:W32/DuckTail.*
Trojan:W32/SuspiciousDownload.A!DeepGuard
Trojan:W32/WindowsDefenderExclusion.A!DeepGuard
Malicious certificate blocking
Mitigation
We recommend reviewing users added to your Facebook Business account through Meta’s Business Manager and revoking access for unknown users that were granted Admin access (with finance editor role).
As the malware exfiltrates all the stolen browser cookies, we recommend terminating all browser authentication sessions and resetting your existing login credentials.