Vulnerability management – seeing the woods for the trees
Risk-based asset scoring gives you the ability to prioritize your threats and help you combat the biggest risks to your company. We explain how.

The number of vulnerabilities has increased steadily over the past couple of years. Not only is the threat landscape increasing in size, but recent global events have also meant that employees are spending much more time out of the office.
As technology continues to improve at breakneck speed, these vulnerabilities creep into our everyday lives – often without being noticed.
Before we begin, let’s make one thing clear: it is very unlikely that you can fix every single vulnerability. Therefore, it is crucial to discover your accepted risk level. By doing so, you can prioritize your risk appetite while making conscious decisions of what to leave untouched considering your available resources.
Low-hanging fruit vs. zero-day exploits
There’s a lot of buzz around zero-day exploits in today’s cyber world. These are software vulnerabilities that cyber attackers have identified but vendors have yet to offer a patch for.
At the same time, even the most advanced attackers are constantly on the lookout for low-hanging fruit. These are the common vulnerabilities in everyday IT tools that may have been present for quite a while without being detected. The attackers scan these security loopholes for entryways with loose targeting. This calls for every organization to engage in proactive vulnerability management and remediation.
Effectively protecting your environment calls for a logical process. You need to begin by identifying exactly where your weak spots are located – which, once again, calls for thorough visibility into your attack surface .
After you have achieved this, the next question is: where do I begin? Often, the number of open vulnerabilities is too high to keep up with, especially in large and complex environments. This is especially true if vulnerability management is not performed as a continuous program.
Further, your company is unique – there is not another like it on the face of the planet. Therefore, you have a unique set of circumstances and requirements. This means that prioritizing remediation efforts based on vulnerability severity or generic vulnerability simply doesn’t work. To have the biggest impact, you need to focus your remediation efforts on assets where the risks are highest for you.
“It is important to utilize the limited time you have available. Using the risk score evaluation, you can really take asset context into account and build a top-down list,” says Dominik Sadowczyk, WithSecure’s Senior Product Manager.
We know our customers. If they’re using one Microsoft program, it is very likely they are using many more – that’s how the offering works. So, we made sure that if a problem in one service, it will automatically be identified in others as well without waiting for the scan to finish. This means it is far more efficient, while adding value by minimizing risk.
It also works the other way around. If you don’t want to block a file and choose to release it from quarantine, the next time we encounter this file, across any other service, it will be ignored, saving time and energy.
“Imagine you’re an admin and you’ve got a file on SharePoint that you want to trust. You then release it. However, tomorrow someone else in the organization shares it on OneDrive. You won’t have to go through the whole process again, as we can remember its classification,” explains Alfital.
By not charging for OneDrive and SharePoint protection separately, the security of your entire ecosystem is covered – giving you the best possible chance of staying safe.
Make informed decisions
Let’s take a look at how to optimize your operations by fixing security vulnerabilities across your attack surface:
- Fix the vulnerabilities with the highest risk
- Aim to fix the highest-risk vulnerabilities as fast as you can to minimize the window of opportunity for attackers
- Deprioritize the ones that pose the least threat to your organization according to your risk appetite
This approach is called risk-based vulnerability management, in which contextual threat data and potential business impact is included in vulnerability risk calculations. This approach ensures that you don’t get lost in the numbers and figures, but instead secure the best business outcomes by, for example, effectively protecting your business-critical assets.
In practice
Risk-based vulnerability management sets some requirements for your vulnerability assessment tool choices, which can only be a positive thing.
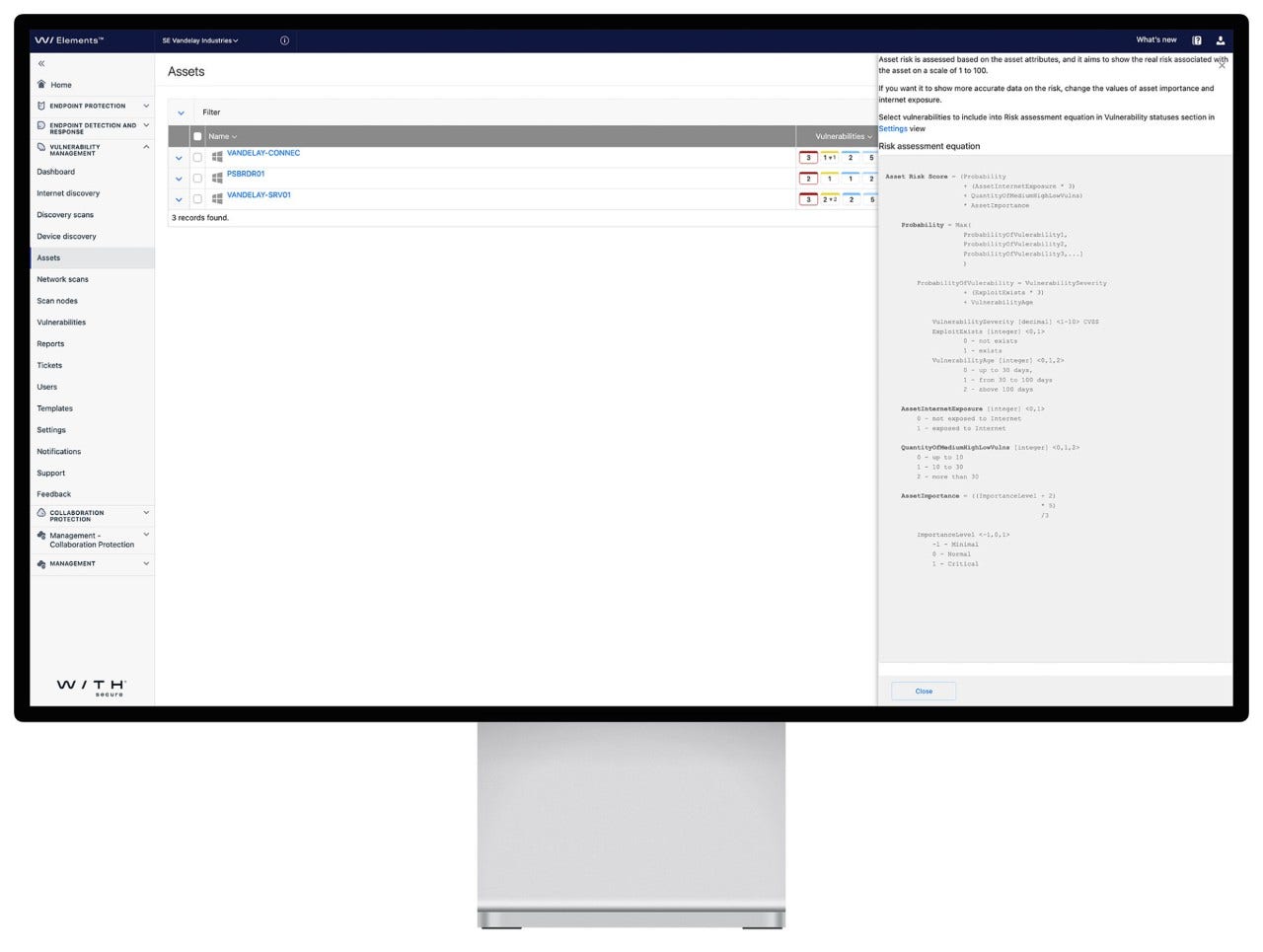
For example, WithSecure Elements Vulnerability Management saves you time by helping to intelligently prioritize remediation work based on each vulnerability’s real level of risk. The asset risk score is calculated using on the asset’s attributesdifferent threat indicators, including:
- Vulnerability severity and age
- The asset’s Internet exposure
- Exploitability
- Internal and contextual asset importance level
- Vulnerability statusYour CIA triad (confidentiality, integrity, and availability) attributes of each asset.
“Start with the most critical assets, as there will be only a few of those – domain controller, key important services and databases, CEO laptop, etc., Assign them manually and they start working your way down the list, improving or changing the asset importance attributes as you go,” Sadowczyk continues.
For example
A practical example of what could go wrong without this risk-based approach is when there’s a long queue of vulnerabilities to fix and assets with high-severity vulnerabilities rise to the top of your priority list.
However, by taking a closer look you may discover that the asset is not even connected to the Internet – in fact, it may not even be in use. On the other hand, there could be a different asset that plays a large role in the day-to-day running of your business operations.
This could have a series of less severe exploitable vulnerabilities but remain unnoticed due to a lack of contextual evaluation.
“Imagine that someone on the public Internet is saying that a particular vulnerability is very, very important, and has the highest score. But in your environment, it's not necessarily the case. Here, it is crucial to not spend time on an issue that is not important to you, as you could be neglecting another, more serious, threat,” Sadowczyk confirms.
So, what is next for vulnerability management at WithSecure? “External threat indicators. We will be able to information from endpoints and external sources and decipher whether a particular vulnerability on your list is more of a threat than it appears, due to, for example, an ongoing hacking activity or malware spread. But more on that soon,” Sadowczyk concludes.